&uuid=(email))
&uuid=(email))
&uuid=(email))
|
|

Editor's Note:
Hey Sr. LP Exec's
Great developmental experience
for Your Team Members!
Supporting Diversity in LP Starts With You
Let's Make a Difference Today
&uuid=(email))
&uuid=(email))
&uuid=(email))
&uuid=(email))

&uuid=(email))
&uuid=(email))

&uuid=(email))
&uuid=(email))
&uuid=(email))
&uuid=(email))



&uuid=(email))








|
|
&uuid=(email))
 |
|
|
 |
See All the Executives 'Moving Up' Here |
Submit Your New Corporate Hires/Promotions or New Position
|
&uuid=(email))
|
|
|
&uuid=(email)) 
|
|
|
Leading Australia and New Zealand retailer, Kathmandu, deploys ShopperTrak
Analytics from Sensormatic Solutions
 Outdoor
adventure destination uses shopper traffic counting solution to make better
informed decisions Outdoor
adventure destination uses shopper traffic counting solution to make better
informed decisions
Johnson Controls today announced that
Sensormatic Solutions,
its leading global retail solutions portfolio, is deploying the ShopperTrak
retail traffic solution with advanced analytics to help
Kathmandu make
data-driven decisions in everything from marketing campaigns to managing staff
schedules to operational effectiveness.
A market leader with over 160 stores across Australia and New Zealand, Kathmandu
offers innovative outdoor apparel and gear designed for rugged landscapes and
adventure-seeking consumers. As retailers today are reimagining their businesses
with advanced technologies that present meaningful customer engagement
opportunities and create a direct path toward higher profit margins, Kathmandu
is no exception.
sensormatic.com
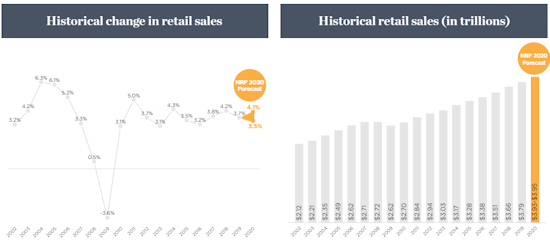
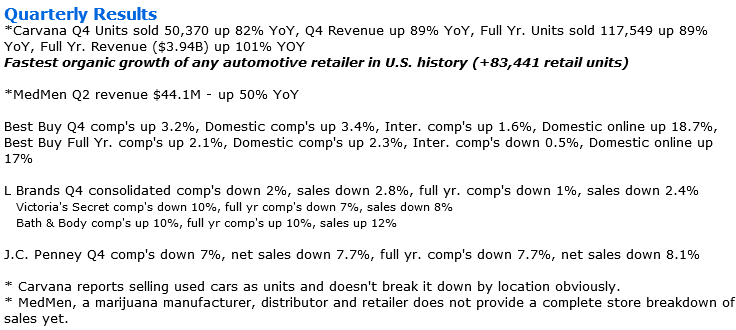
Retail sales expected to climb between 3.5% and 4.1% in 2020, unless coronavirus
derails growth, NRF says
 Retail
sales in 2020 are forecast to rise between 3.5% and 4.1%, topping $3.9 trillion,
despite the headwinds of a lingering trade war, the coronavirus outbreak and an
upcoming presidential election, the industry's trade group said Tuesday. Retail
sales in 2020 are forecast to rise between 3.5% and 4.1%, topping $3.9 trillion,
despite the headwinds of a lingering trade war, the coronavirus outbreak and an
upcoming presidential election, the industry's trade group said Tuesday.
"The nation's record-long economic expansion is continuing, and consumers remain
the drivers of that expansion," National Retail Federation President and CEO
Matthew Shay said in a statement.
NRF said its 2020 forecast assumes the coronavirus does not become a global
pandemic.
"We are not seeing any deterioration in the financial health of the consumer,"
NRF Chief Economist Jack Kleinhenz said. "Consumers are in better shape than any
time in the last few years. Most important for the year ahead will be the
ongoing strength in the job market, which will support the consumer income and
spending that are both key drivers of the economy. The bottom line is that the
economy is in a good place despite the ups and downs of the stock market and
other uncertainties. Growth remains solid."
nrf.com
Coronavirus Update
Coronavirus is Officially Here
With 1st "Community Spread" Case in Sacramento
CDC warns to prepare for spread of coronavirus symptoms, cases
 U.S.
health officials issued what appears to be a strong warning about novel
coronavirus on Tuesday - it is not a matter of if, but when it will spread in
communities in the U.S. and that Americans should prepare for "significant
disruption" to their lives as a result of the virus. U.S.
health officials issued what appears to be a strong warning about novel
coronavirus on Tuesday - it is not a matter of if, but when it will spread in
communities in the U.S. and that Americans should prepare for "significant
disruption" to their lives as a result of the virus.
"Ultimately, we expect we will see community spread in this country," Dr. Nancy
Messonnier, director of the CDC's National Center for Immunization and
Respiratory Diseases, said at a coronavirus news conference.
Messonnier added that Americans should channel their concern about the
virus, officially called COVID-19, into preparing for its arrival.
Coronavirus Symptoms:
abc7ny.com
 Trump
Requests $1.8 Billion for Coronavirus Response Trump
Requests $1.8 Billion for Coronavirus Response
The request includes $1.25 billion in new spending for the Department of Health
and Human Services, as well as the ability to use $535 million in previously
appropriated funds set aside to fight the Ebola virus. The spending request
would give HHS flexibility in its response, but much of the funding would be
used for vaccines and vaccine development.
associationsnow.com
San Francisco declared a state of emergency over coronavirus
San Francisco Mayor London Breed recently
declared a state of emergency in preparation for a possible coronavirus
outbreak.
businessinsider.com
ASAE Provides Issue Roundup: Coronavirus Disease (COVID-2019) Resources
Key Resources:
•
NAFSA Coronavirus Critical Resources
•
United States Travel Association
Emergency Preparedness and Response: Coronavirus Toolkit
•
U.S. Chamber of Commerce "Understanding
the Coronavirus" webinar
•
World Health Organization
Coronavirus Disease 2019 (COVID-19) Situation Report
•
Centers for Disease Control and Prevention
Coronavirus Disease 2019 (COVID-19) Situation Summary
•
Centers for Disease Control and Prevention
Travel Notices
How coronavirus could force the work-from-home movement
U.S. Companies Discussing It Skyrockets
 In
February so far, 77 public company transcripts mention "work from home" or
"working from home," according to financial data platform
Sentieo. That's up from just four mentions of the phrase in the same month a
year ago. The vast majority of those documents also mention coronavirus. In
February so far, 77 public company transcripts mention "work from home" or
"working from home," according to financial data platform
Sentieo. That's up from just four mentions of the phrase in the same month a
year ago. The vast majority of those documents also mention coronavirus.
Remote workers make up anywhere from
about 5 percent (those who typically work from home) to
nearly two-thirds (who sometimes work remotely) of the workforce, depending
on the measurement. What's certain is that the trend has been ticking up and a
pandemic like coronavirus has the potential to fast-track the move by making it
more universally accepted and prominent.
redcode.com
CSO: A security guide for pandemic planning: 7 key steps
Poll: Most Americans Concerned There Will Be a Major Coronavirus Outbreak in the
U.S.
Zebra Donates Technology to China Hospitals to Assist in Epidemic Prevention
Efforts
New York: Coronavirus concerns land 83 in voluntary isolation in Nassau County
Stay up to date on the CDC's website: https://www.cdc.gov/coronavirus/2019-ncov
Clearview AI Facial
Recognition
Hacked - Sued - Getting Grilled by Congress
Clearview AI, the world's scariest facial recognition
company, can't even keep its own data secure
Clearview AI has recently attracted
criticism from Congress for its cavalier use of facial recognition technology.
Clearview AI, the controversial and secretive facial recognition company,
just experienced its first major data breach - a scary prospect considering
the sheer amount and scope of personal information in its database, as well
as the fact that access to it is supposed to be restricted to law enforcement
agencies.
According to a memo sent to its customers which was
obtained by the Daily Beast, an intruder gained "unauthorized access" to the
company's client list, its number of user accounts, and a number of searches its
customers have conducted. That client list might be particularly sensitive, as
Clearview claims it works with hundreds of federal and state law enforcement
agencies. (A
BuzzFeed News report said those numbers are inflated.)
The good news is that there is no evidence that Clearview's database of 3
billion photos was hacked. But the fact that the company could be breached at
all is worrisome enough. Clearview says it obtained these photos by scraping
publicly available images from all over the internet. The company's software
uses proprietary facial recognition technology to help law enforcement agencies
identify suspects by matching their images with those in the database.
redcode.com
Clearview AI Facial Recogniton Database Hacked
Entire Client Files Stolen
 A
new facial recognition company, which claims to be used by over
600 law enforcement agencies, has suffered a data breach, according to
the company. A
new facial recognition company, which claims to be used by over
600 law enforcement agencies, has suffered a data breach, according to
the company.
Clearview AI confirmed with Fox News that its entire client list was stolen
in the breach. According to the company, someone gained access to a list
of all of Clearview's customers, the number of accounts used by those customers
and the number of searches they have conducted.
The software, first outed in a
New York Times investigation earlier this year, claims to identify anyone
with just a single image by instantly running an image through its database of
over 3 billion internet photos. Law enforcement agencies had been using the app
in secret, and have reported how accurate and helpful the technology has been in
identifying suspects.
This breach is significant in that privacy advocates, and some law
enforcement officials, have voiced cybersecurity concerns about the brand
new app's potential vulnerability to hacking. Clearview AI stopped short of
calling this incident a hack.
Gurbir Grewal, the attorney general of New Jersey, has temporarily banned the
application in the state's police departments, citing cybersecurity and privacy
concerns, despite the fact that the application already has been used by one
department to help identify a pedophile. Article continues
here.
Clearview AI Class Action Lawsuit Over Privacy Concerns - Willful, Reckless &
Negligent
Scraping Internet Images isn't Facial
Recognition
Click here
to read today's full Clearview AI coverage
Payroll Scrutinized Drug Store Industry Scandal in the News Again
Walgreens embroiled in a stressed-out pharmacist scandal
Deleting Bullet Points - Removing Slides
From Audit Presentation
 Walgreens
pharmacists have complained of being overwhelmed with work to the point of
making errors, but a report seems to indicate that this was a message the
retailer wanted to keep hidden from the public. Walgreens
pharmacists have complained of being overwhelmed with work to the point of
making errors, but a report seems to indicate that this was a message the
retailer wanted to keep hidden from the public.
Last year, business consultancy Tata Consulting Services, which was working with
Walgreens, discovered stressed-out, overworked pharmacists who attributed their
mistakes to unreasonable workplace expectations at the stores, according to a
New York Times article. Emails and chat logs, however, reveal that
consultants were advised to keep that information out of a report that was
presented this month.
Amy Bixler, director of pharmacy and retail operations at Walgreens, directed
the consultants to delete a bullet point in a presentation that addressed
how pharmacists ignore proper procedure in order to meet corporate metrics.
One of the slides which directly addressed pharmacists making stress-related
errors was also removed.
The retailer is not alone among pharmacies, however, in facing accusations of
putting the public at risk due to the pressure they put on pharmacists,
according to the Times. CVS and other major chains have drawn similar heat, with
pharmacies described as "understaffed" and "chaotic."
Walgreens worked last year to disentangle itself from a different scandal
- its erstwhile partnership with fraudulent medical testing startup Theranos.
In May of 2019, the chain faced a shareholder lawsuit over a perceived failure
to vet Theranos, according to Bloomberg Law. Walgreens called for the
lawsuit to be thrown out.
retailwire.com
Reputation Lost Business for Scandalized Nygard Brand
Dillard's, with nearly 300 locations, has
cancelled all orders with company founded by Canadian fashion mogul

Dillard's cutting business over recent sexual assault allegations against the
company's founder, Peter Nygard.
The women are accusing the clothing company founder of raping them at his
mansion in the Bahamas and operating what they say is a "sex trafficking
ring."
"In light of the serious allegations concerning Peter Nygard, which are in
direct opposition to our core values, Dillard's has refused current deliveries,
cancelled all existing orders and suspended all future purchases from Nygard,"
Dillard's said in an emailed statement on Wednesday.
cbc.ca
4 Best Practices for Second-Chance Hiring
How to successfully hire candidates with
criminal records
Today, two-thirds of HR professionals surveyed reported that their companies
have hired people with a criminal record, with only 14 percent of respondents
saying they would be unwilling to hire such an applicant.
&uuid=(email)) Here
are strategies that can help organizations make the best hires with the best
outcomes. Here
are strategies that can help organizations make the best hires with the best
outcomes.
Make second-chance hiring part of your corporate culture. Second-chance
hiring is less likely to work if an organization is doing it for the wrong
reasons.
It's also important to note that-for those companies that have hired
second-chance candidates- 82 percent of hiring managers said the quality of
those candidates is as good as, if not better than, someone without a criminal
record, said Richard Bronson, CEO of 70 Million Jobs, a job-search site
dedicated to this population.
Provide training and work support.
Establish mentoring. Fewer than 3 in 10 companies have a formal mentoring
program, but research has shown that it can improve employee retention rates and
boost employee satisfaction. The practice is even more beneficial for
second-chance candidates since it can help those employees feel like part of the
organization more quickly and help them avoid common job pitfalls,
Default to transparency-but keep employee details confidential. You might
think that it's important to let managers and executives know which new hires
have prison records, but this is a very bad idea, Martin said. "The HR team
should treat that information like a medical condition. Very rarely should
anyone know about it," she said.
That doesn't mean you don't talk about the initiative, though, Bronson said.
While people have a right to privacy, you still need to let current employees
know that you're embracing second-chance hiring and why you're doing it. The
facts regarding hiring those with records are much different than the widely
held negative biases. Educate your workforce on why you're accessing this pool
of talent. Let them share ownership [and] they'll also be sharing pride."
shrm.org
SHRM's Workplace Violence Resource Center
The Society of Human Resources provides resources and educational programs for a
host of subject as one might expect.
Certainly, all of which discuss the subjects from the HR prospective. An
important channel to the organization and to the LP and AP efforts. And the SHRM
is one of the strongest specialty trade associations in the U.S. So they have
the resources to produce great content. Content that can benefit our community.
Just a thought. -Gus Downing
Stage Stores Cuts Jobs HQ & Closing 60 of Gordman's stores
National Restaurant Association Releases 2020 State of the Restaurant Industry
Report

|
|

|
All the News - One Place - One Source - One Time
Thanks to our sponsors/partners - Take the time to thank them as well please.
If it wasn't for them The Daily wouldn't be here every day for you.
|
|
&uuid=(email))
|
|
 |
|

|
|

Finding and managing your
video
just got faster and easier!
OWS Version 2.0, a huge step forward in
both performance and features, is designed to make finding video and managing
your video surveillance system faster and easier.
See the full
list of features available in OWS 2.0.
Take a live demo
tour of the new features in OWS 2.0.


 |
|

&uuid=(email)) |
|
&uuid=(email))
|
|
RSA
Conference - Day 3 Recap
Keynote Highlights, Early Stage Expo, Launch Pad, and More
 Another exciting day at RSAC in the books! We've learned a lot in the past few
days and shared some incredible moments, from hearing the exciting tales of
sailing around the world and travels in space to witnessing many fantastic
speakers discuss the latest in cybersecurity.
We're officially past the halfway mark, but the fun isn't over just yet. Let's
see what took place on Day 3. Another exciting day at RSAC in the books! We've learned a lot in the past few
days and shared some incredible moments, from hearing the exciting tales of
sailing around the world and travels in space to witnessing many fantastic
speakers discuss the latest in cybersecurity.
We're officially past the halfway mark, but the fun isn't over just yet. Let's
see what took place on Day 3.
 Nine keynotes took the South and West stages. The day opened with
Hacking Exposed: Global Threat Brief, where attendees heard Dmitri
Alperovitch, co-founder of Crowdstrike, discuss the most novel attacks in the
current global landscape, including the cyber strategies of various nation
states. "Policy is the next frontier," shared Alperovitch. "Norms are
established by government inaction or action, and in the coming years,
government regulation, like GDPR, CCPA, Section 230 and national data breach
laws, among others, establishes what sort of attacks we tolerate and which we do
not." Nine keynotes took the South and West stages. The day opened with
Hacking Exposed: Global Threat Brief, where attendees heard Dmitri
Alperovitch, co-founder of Crowdstrike, discuss the most novel attacks in the
current global landscape, including the cyber strategies of various nation
states. "Policy is the next frontier," shared Alperovitch. "Norms are
established by government inaction or action, and in the coming years,
government regulation, like GDPR, CCPA, Section 230 and national data breach
laws, among others, establishes what sort of attacks we tolerate and which we do
not."
The
Genomics: A New Frontier for Privacy and Security panel featured a
wide-range of experts representing the healthcare, security and genetic testing
industries. They explored the opportunities and challenges of genomics for
individuals, companies and law enforcement, all with unique privacy
implications.
Sharon Terry, President and CEO of Genetic Alliance, said, "Consumers must be
the central focus and rewarded for sharing this information," while Kathy Hibbs,
Chief Legal and Regulatory Officer of 23andMe, noted that the company's
customers "spend the most time on the privacy page of our website." Mike Wilson, SVP and Chief Security Officer of Molina Healthcare, wrapped up the discussion
by saying that "privacy is largely a philosophical discussion and should
continue as this technology evolves."
 In an afternoon keynote,
Navigating Privacy in a Data-Driven World: Treating Privacy as a Human Right,
Jules Polonetsky, Chief Executive Officer at the Future of Privacy Forum,
discussed why privacy is a basic human right in the ever-evolving technology
industry. Jules explored how society is at a tipping point because new high-tech
products like drones or biometric clothing are integrating themselves in our
lives and, as the world around becomes more advanced, society must adjust. To
protect consumer privacy, he argued, new legislation needs to be created because
"if we mess up the same way we messed up with cookies" it will be similar but
worse.
rsaconference.com In an afternoon keynote,
Navigating Privacy in a Data-Driven World: Treating Privacy as a Human Right,
Jules Polonetsky, Chief Executive Officer at the Future of Privacy Forum,
discussed why privacy is a basic human right in the ever-evolving technology
industry. Jules explored how society is at a tipping point because new high-tech
products like drones or biometric clothing are integrating themselves in our
lives and, as the world around becomes more advanced, society must adjust. To
protect consumer privacy, he argued, new legislation needs to be created because
"if we mess up the same way we messed up with cookies" it will be similar but
worse.
rsaconference.com
NIST Releases Roadmap to Creating Partnerships to Build the Cybersecurity
Workforce
Partnerships to Build the Cybersecurity
Workforce
The National Institute for Standards and Technology (NIST) released a report
outlining best practices in building the cybersecurity workforce through
regional partnerships.
The National Initiative for Cybersecurity Education (NICE) is addressing the
critical issue by energizing and promoting a robust network and ecosystem of
cybersecurity education, training, and workforce development. Supporting this
mission, objective 3.3 of the NICE Strategic Plan emphasizes guiding career
development and workforce planning by facilitating state and regional consortia
to identify cybersecurity pathways addressing local workforce needs.
According to NIST, "This publication was created for those seeking guidance on
how to organize and facilitate regional efforts to enhance cybersecurity
education and workforce development. While this document explores some elements
for consideration when forming alliances, it is not intended to be a how-to
guide that gives specific instructions. NIST believes that this is best left to
the local or regional experts who are familiar with the needs of their specific
community."
(NIST) is pleased to announce the NIST Internal Report (NISTIR) 8287:
A Roadmap for Successful Regional Alliances and Multistakeholder Partnerships to
Build the Cybersecurity Workforce.
Click here to access full report.
nist.gov
Modified Draft CCPA Regulations: How They Impact Businesses
 A
Privacy Expert Sorts Through the Clarifications of Law's Requirements A
Privacy Expert Sorts Through the Clarifications of Law's Requirements
California Attorney General Xavier Becerra recently issued
modified draft regulations to carry out the
California Consumer Privacy Act that are designed to help businesses take a
more pragmatic approach to privacy. The proposed regulations clarify, for
example, that businesses are not obligated to search for personal information in
response to a consumer's request if certain conditions are met, says
Caitlin Fennessy, research director at the International Association of
Privacy Professionals.
govinfosecurity.com
Ensure Your Cloud Security Is as Modern as Your Business
After speaking with CISOs, CTOs, and chief data officers, it's clear to me that
we're still not speaking the language of cloud security in a way
everybody can easily understand.
In addition, clarity is missing on who owns what part of cloud security
and who is doing the necessary work to maintain it throughout the organization.
It doesn't help that there is hidden or abstracted complexity in cloud platforms
that's difficult to account for at all times. Combined with the rapid pace of
technology change in general and the pressure that comes from the "push to
production" in typical organizations, these factors all add to the overall risk
we face in the cloud.
Here are three steps to consider that will make sure your cloud security is as
modern as your business:
1. Converge Your People
Align your IT decision-makers and your IT organization around an end-to-end view
of infrastructure security and information protection that includes cloud
environments. Start by standardizing the language used to discuss cloud
and data security. It's the first step in furthering your organization's
collective understanding.
2. Converge Your Services and Tools
On the cloud development side, there has been an explosion of tools and
services being built for specific purposes. While many of these are consumed
as managed services, they introduce a new demand on resources and potentially
can increase risk. This is likely to continue until we see simplification and
convergence.
3. Plan for a Data-Fluid Future
Adopting the cloud means your organization's data moves between users, apps, and
cloud environments in more dynamic ways. All of this requires a data-centric
approach to security protocols. Deciding to migrate workloads or adopt new
cloud applications is the easy part; maintaining the right level of
corresponding permissions and policies won't happen without a clear cloud
security and information protection strategy.
There's no magic bullet for getting cloud security right. Take a
comprehensive approach to better protect your organization. Security hygiene is
still a must, but also look at your risk posture through a data protection lens
and implement DLP and behavioral analytics.
darkreading.com
Insider Threat & The Cloud
Cloud-based collaboration tools are a major driver of data exfiltration
Cloud-based collaboration technologies and workforce turnover have become major
drivers of data exfiltration as insider threat programs fail to keep pace with
today's digital workplace, a Code42 survey reveals.
&uuid=(email)) "When
it comes to data loss, leak and theft, for too many companies, the inside is
their blindside," said Joe Payne, Code42's president and CEO. "Insider
threat programs are not keeping up with today's collaborative work culture.
People and data are on the move now more than ever. Workers are switching jobs,
and company files are being uploaded to the web, emailed as attachments and
synched to personal cloud accounts." "When
it comes to data loss, leak and theft, for too many companies, the inside is
their blindside," said Joe Payne, Code42's president and CEO. "Insider
threat programs are not keeping up with today's collaborative work culture.
People and data are on the move now more than ever. Workers are switching jobs,
and company files are being uploaded to the web, emailed as attachments and
synched to personal cloud accounts."
Workers opt for unsanctioned collaboration tools to share company files
Cloud-based collaboration tools have changed the workplace. As part of their
regular work routines, employees are emailing, airdropping, messaging and
slacking from desktops, mobile devices, on the road and in coffee shops.
According to the report, workers routinely use both authorized and unauthorized
cloud-based platforms to share files and ideas with colleagues. They
sidestep sanctioned tools because they believe they are too complicated,
restrictive and slow-or don't have enough features.
Thirty-seven percent (37%) of workers use unauthorized apps daily while
26% use them weekly to share files with colleagues
Collaboration tools rated among top vectors for data exfiltration
While technology has made it easy for employees to share files legitimately via
personal email and the cloud, it's also made it easier for them to exfiltrate -
or even infiltrate - data like product ideas, source code and customer lists.
The risk of
insider threat incidents is heightened because the very tools that workers
use to collaborate are some of the most popular vectors for data exfiltration.
Insider threat programs earn a failing mark as workers change jobs
The simple act of
changing jobs can tempt employees to take company data - and workers are
changing jobs more frequently than ever. Security teams continue to grapple with
how to effectively deal with data theft and misuse - whether accidental or
intentional - when employees depart.
As workers move from company to company, they admit that they have not only
taken data with them, they have done it more than once. The consequences of this
behavior are even more damaging to a business when workers take data from a
former employer and go to work for a competitor.
•
Two-thirds (63%) of respondents who said they have
taken data are repeat offenders
•
One-third (32%) of respondents who had infiltrated
data were encouraged by their new employers to share it with new colleagues.
helpnetsecurity.com
New York City Bill Aims to Regulate AI Hiring Tools
Decathlon, the world's largest sporting goods retailer exposes employee,
customer data

|
&uuid=(email)) |
|
|
&uuid=(email))
|
|
Leak of 30,000 cannabis customer records heightens need for
effective data security
A recent leak of 85,000 cannabis dispensary files, including 30,0000 customer
records, has put dispensaries and other industry stakeholders under pressure
to fortify their systems and processes to comply with data privacy regulations
and laws.
Cybercriminals are increasingly infiltrating third-party partners and supply
chains as a means to gain a foothold in an organization's networks and systems.
Threat actors look for weak links to gain access to sensitive data, and once
they do, they can restrict access to critical data in a ransomware attack or
disrupt the business from an operations perspective. As cannabis enterprises
move from siloed, manual processes to connected technologies and more
sophisticated automated operations, they open themselves to these and other
types of attacks.
cannabisbusinessexecutive.com
Cannabis store robberies prompt retailers to remove legislated window coverings
"Nobody should be in jeopardy at their
work."
A series of cannabis store robberies in Alberta has led some retailers to
tear down window coverings initially erected to satisfy federal legislation.
Those visual obstructions were meant to adhere to the Cannabis Act to keep
cannabis products and accessories out of the view of minors.
But retailer Nathan Mison said those window coverings compromise the safety
of staff by making it easier for robbers to commit their crimes.
calgaryherald.com
Cannabis Around the World, Part
II: The Common Era
 By
Tony Gallo, Managing Partner & Katharine Baxter,
Lead Technical Writer for Sapphire Risk Advisory Group By
Tony Gallo, Managing Partner & Katharine Baxter,
Lead Technical Writer for Sapphire Risk Advisory Group
The beginning of the Common Era saw a focus on cannabis as a medicinal aid
from many societies. In ancient China, one of the oldest official medical
texts ever discovered, the Shennong Bencao Jing (The Classic of Herbal
Medicine), describes cannabis use for pain relief. The text dictates that
cannabis, which had become a major crop in the region, should be ground into
paste and could be consumed topically and orally. The Chinese continued to
utilize cannabis in medicine, with physicians eventually using the plant for
anesthesia as well as for a variety of other disorders.
 An
emphasis on cannabis for medical purposes also became popular throughout the
Roman Empire by the Common Era. Roman medical texts from this period explain the
plant's use for external wounds, tumors, abdominal pain, and inflammation.
Writings also depict cannabis' use recreationally as an intoxicant in the
ancient Roman culture. An
emphasis on cannabis for medical purposes also became popular throughout the
Roman Empire by the Common Era. Roman medical texts from this period explain the
plant's use for external wounds, tumors, abdominal pain, and inflammation.
Writings also depict cannabis' use recreationally as an intoxicant in the
ancient Roman culture.
Cannabis also became widespread in the Middle East for its medicinal and
recreational uses. Medicinally, cannabis and hemp were used to cure skin
diseases, alleviate pain, and treat parasitic worms among other internal
ailments. The plant also become popular as hashish, which was frequently smoked
recreationally because Islam forbid alcohol, but did not explicitly ban
cannabis.
Read more
Trump Dumps on Medical Cannabis (Again)
Illinois recreational weed sales net $10M in tax revenue in 1st month
Hobo Cannabis Company Announces Ontario Expansion Plan, Bringing Market Share to
15 Locations |
|
&uuid=(email))
|
|
|
|
&uuid=(email)) |
|
|

&uuid=(email))
|
|
|
How FIs Can Win The Battle Against 'Smarter' Payments Fraud
With the evolution of fraud, the detection and prevention efforts also change.
As Lerdal told PYMNTS, there's no one-size-fits-all approach when it comes to
fighting attacks. When establishing the foundation of an effective FI
cybersecurity program, though, he said it's important to have a culture in place
with a set of rules for different modes of transactions.
Before eCommerce truly took root, much of fraud mitigation centered around what
he termed "velocity counters." Five transactions made in a short period of
time would have raised red flags for merchants at one time. Today, however,
that velocity is fairly commonplace.
In looking for activities that can point to anomalous behavior at a specific
point of transaction, governed by a set of rules, Lerdal pointed to
ATM-slamming. This is when an ATM that typically does five transactions per hour
from 8 a.m. to 5 p.m., then three transactions per hour after 5 p.m., suddenly
shows 50 to 100 transactions in a burst of minutes.
For the FI that has such a compromised machine in the field, he said, "you
want to make sure you have the tools to identify that activity and shut it down."
pymnts.com
Target, Eschewing Amazon's Open Marketplace, Is Making Strides In E-Commerce
- Target surpasses three
competitors to crack top 10
- Amazon, Walmart & eBay lead the pack
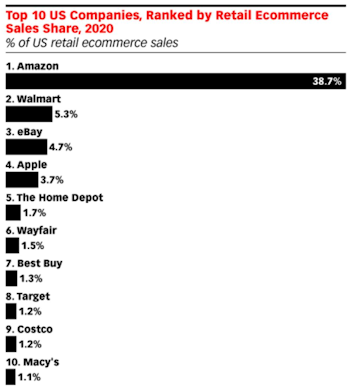
Today, eMarketer reported that Target has surpassed three competitors to become
the eighth-largest retailer in the U.S. in terms of e-commerce sales, up from
11th place just one year ago.
While Amazon and Walmart rely heavily on a marketplace model for e-commerce
growth, Target appears to be focusing more on its first-party assortment, which
can be fulfilled by stores.
Target's e-commerce marketplace (known as Target+ or Target Plus) assortment is
highly curated, as opposed to Walmart and certainly to Amazon. Amazon in
particular has an open-door policy for new sellers. It's straightforward to set
up a new Seller account and start listing products almost immediately. Walmart
has some additional screening requirements to validate the capabilities of new
sellers. But Target is on a whole new level: Brands can only start selling on
the marketplace if they are invited to do so. And those invites are definitely
exclusive. The invite-only marketplace started with 30 merchants, and six months
later has grown to just 60 merchants and 115,000 products as of the end of 2019,
according to Marketplace Pulse data.
forbes.com
Walmart steps up competition with Amazon by fulfilling orders for third-party
vendors |
|
&uuid=(email))
|
|
|
|
&uuid=(email)) |
|
|
|
&uuid=(email))
|
|
Hobart, IN: Five Men accused of shoplifting punched Macy's LP, led police on
chase
Charges filed Tuesday against five people allege they worked together to
shoplift items from a store at Southlake Mall, punched two loss prevention
officers who attempted to stop them and hit two cars during a police chase. The
five men, all of Chicago, are accused of attempting to steal items Feb. 23 from
the Macy's store in Hobart. Thomas, London and Bradley began grabbing items
while Upshaw acted as a lookout and coordinator. Video surveillance showed the
four men met back at an exit, where Thomas allegedly made a call to Branchcomb
to pick them up in her SUV.
The four men bull rushed a loss prevention officer who attempted to stop them
from exiting a set of double doors, and London punched the officer in the face.
Thomas punched a second loss prevention officer, who was attempting to help the
first officer. The first officer was struck several more times in the head, face
and body before the men piled in the SUV, with Thomas driving, and fled. The
driver hit two vehicles at an intersection Police continued to chase the SUV
north on I-65, and Merrillville police deployed a tire-deflating device on a
ramp from I-65. The driver of the SUV hit the Stop Sticks and lost control. The
SUV rolled over onto its roof and came to rest on its wheels. All five
defendants were taken into custody. The two loss prevention officers suffered
possible concussions and soreness as a result of their injuries.
nwitimes.com
Wyandotte, MI: Accused shoplifter fakes illness to avoid arrest; pulled stunt
three times on same day
Police are accustomed to arrestees faking illness to avoid arrest, but one man
took his acting skills to a whole other level. The incident began shortly after
5:30 p.m. Feb. 7 when three officers were sent to Rite Aid, in regards to a
shoplifting incident that had just occurred. Officers found a man matching the
suspect's description walking down the street. An officer asked the 60-year-old
Detroit resident what he was up to. The man put his hands in the air and stated
he "stole some stuff." Police said bulky items were sticking out from the back
of his jacket. As he was patted down, a toothbrush fell out of his jacket.
Police informed the man he was being arrested for retail fraud. As an officer
attempted to place him in handcuffs, the man said he needed to go to the
hospital, and then he started to pass out. An officer returned the items to
Rite Aid. A receipt of the items totaled over $390.
Before paramedics began transporting the accused shoplifter to the hospital, a
paramedic told police that once he was inside the ambulance, he opened his
eyes and asked if police were gone. Hospital staff informed officers that
earlier in the day he was admitted to the hospital after another retail fraud,
but then stated he was fine and didn't need medical attention.
thenewsherald.com
Evansville, IN: Police Officer struggles with a shoplifter in a moving car, man
said, 'I'll kill us both'
A shoplifting incident at Eastland Mall ended with a man and Evansville Police
officer struggling in a moving car through the parking lot as the man screamed,
"I'm going to kill us both." On Wednesday night, a uniformed officer was at
Dillard's when a loss prevention employee told him she saw a man and woman take
items and head toward the exit without paying. Spencer continued resisting
arrest and ran to a car in the parking lot and opened the door on the passenger
side, police said. The officer stood in front of the open passenger door and
tried to arrest Spencer, who continued to shove the officer, and at one point,
the officer fell backward into the vehicle while holding onto Spencer, according
to the police report. Both Spencer and the officer were laying across the front
seats of the car struggling when Spencer managed to start the car, police said.
When the car began to speed up again and the engine sounded louder than it had
at any other point before, the officer said he feared for his life and drew his
gun. At that point, Spencer released the gas pedal and said, "I give up; I'm
sorry," according to the report. The car came to a stop, and Spencer was
arrested. When the officer checked Spencer's driver's status, it came back as
suspended with a prior. The clothing Spencer and the woman had left in the
parking lot were collected by Dillard's employees. The total value of the
merchandise was $1,231.
courierpress.com
Update: St Louis County, MO: Man arrested after $100,000 worth of rare video
games stolen from South County store
UK: Blackburn, England: Shoplifter stole 'expensive' Gaviscon to send to parents
in Romania
Chicago, IL: Three charged with stealing items worth $6000 from Elmhurst Kohl's |
|
|
|
&uuid=(email))
|
|
|
|
&uuid=(email))

|
|
Shootings & Deaths
Five Co-workers killed in Milwaukee Molson Coors attack; shooter dead
 Five
people and the attacker died in a shooting at the MillerCoors campus in
Milwaukee, officials said at a Wednesday evening news conference. The shooter
died from an apparent self-inflicted wound, according to Milwaukee Police Chief
Alfonso Morales. Molson Coors Beverage Company owns the MillerCoors campus in
Milwaukee. Molson Coors CEO Gavin Hattersley posted a statement on Twitter
saying the shooter was an active brewery employee. Officials confirmed the five
people killed were also employees. "This is an unspeakable tragedy for our
city," said Milwaukee Mayor Tom Barrett. More than 1,000 employees were working
at the MillerCoors campus on the city's west side when the shooting occurred.
Police do not yet have a definitive accounting of all the company's staff.
wkow.com Five
people and the attacker died in a shooting at the MillerCoors campus in
Milwaukee, officials said at a Wednesday evening news conference. The shooter
died from an apparent self-inflicted wound, according to Milwaukee Police Chief
Alfonso Morales. Molson Coors Beverage Company owns the MillerCoors campus in
Milwaukee. Molson Coors CEO Gavin Hattersley posted a statement on Twitter
saying the shooter was an active brewery employee. Officials confirmed the five
people killed were also employees. "This is an unspeakable tragedy for our
city," said Milwaukee Mayor Tom Barrett. More than 1,000 employees were working
at the MillerCoors campus on the city's west side when the shooting occurred.
Police do not yet have a definitive accounting of all the company's staff.
wkow.com
Cleveland, OH: One dead, another injured in Gas station shooting
Police said the suspect tried to get into the gas station and pulled out a gun
when employees didn't let him inside. As the suspect was leaving, a 53-year-old
man inside the store got his own handgun and followed him. Cleveland police said
that's when the suspect turned and fired multiple shots, hitting two others. A
37-year-old man suffered a gunshot wound to the chest and died. A bullet grazed
the chest of a 55-year-old.
fox8.com
Update: Madison, WI: 3 Arrested following shots fired at Walmart
A $1 million bond in connection with shots fired during a shoplifting incident
at Walmart late last week has been set for a Jackson man. Paul C. Barnett, 37,
of Jackson, has been charged with felony shoplifting, simple assault by threat,
discharge of a firearm, resisting arrest and possession of a firearm by a
convicted felon. MPD has two others in custody. Stephanie A. Collom, 27, of
Jackson, will be charged with accessory to felony shoplifting and Conerly
Chapman, 33, of Jackson, has also been charged with accessory to felony
shoplifting. The trio had tried to make off with roughly $2,000 in Walmart
merchandise. All three suspects remain in the Madison County Detention
Center.
Newman said that on Feb. 20 police received information from Loss Prevention
employees of Walmart that there was a male subject shoplifting in the store.
As the male subject approached the grocery exit of the store the loss prevention
employees identified themselves in an attempt to stop him at which time the male
subject exited the store into the parking lot, produced a handgun and fired two
shots in the air.
onlinemadison.com
Robberies, Incidents & Thefts
Tampa, FL: Body cam video captures arrest of woman accused of making bomb in
Tampa Walmart
 An
off-duty Florida Fish and Wildlife Conservation officer had his body-worn camera
recording when he took into custody the woman accused of building a homemade
bomb with supplies from a Walmart. 8 On Your Side is the first station to obtain
the new video from the Jan. 11 arrest of 37-year-old Emily Stallard at Walmart .
"So the reason you're in handcuffs right now is for the mason jar filled with
nails and kerosene that you constructed," Officer Reece Alvis tells Stallard
after she's taken outside the store. "That wasn't mine," Stallard said. "If
there's something like that it wasn't mine." "Well they have video of you
putting that together," the officer said. When Officer Alvis approaches Stallard
and identifies himself, Stallard is with her son and seen holding a lighter in
her right hand. "Well go ahead, put your phone down, purse down the lighter,"
Officer Alvis tells Stallard before putting her in handcuffs. An
off-duty Florida Fish and Wildlife Conservation officer had his body-worn camera
recording when he took into custody the woman accused of building a homemade
bomb with supplies from a Walmart. 8 On Your Side is the first station to obtain
the new video from the Jan. 11 arrest of 37-year-old Emily Stallard at Walmart .
"So the reason you're in handcuffs right now is for the mason jar filled with
nails and kerosene that you constructed," Officer Reece Alvis tells Stallard
after she's taken outside the store. "That wasn't mine," Stallard said. "If
there's something like that it wasn't mine." "Well they have video of you
putting that together," the officer said. When Officer Alvis approaches Stallard
and identifies himself, Stallard is with her son and seen holding a lighter in
her right hand. "Well go ahead, put your phone down, purse down the lighter,"
Officer Alvis tells Stallard before putting her in handcuffs.
According to the criminal report affidavit: "The defendant used a shoelace as a
wick and attempted to light the shoelace with a lighter, intending to cause
damages by means of fire to the Walmart store and citizens." In the body camera
video, deputies arrive shortly after the FWC officer escorts Stallard and her
son out of the store. He later returns to the store's security room and takes
photos of a shopping cart with mason jars, denatured alcohol and nails. Deputies
arrested Stallard for attempted arson of a structure, fire bombing, child Aabuse
and contributing to the delinquency of a minor.
wfla.com
North Miami, FL: Police standoff with a man shouting from a McDonald's roof is
over
A man who was throwing items off the roof of a McDonald's just south of North
Miami was taken into custody early Wednesday. When officers arrived, the man
began shouting and throwing objects at them from the roof, police said. One of
the items was a hammer. While he was "distracted," special unit forces snuck up
onto the roof using another entrance and took him into custody shortly after
6:30 a.m., a police spokesman said.
miamiherald.com
&uuid=(email)) Update:
North Olmsted, OH: Police Officer hit by fleeing car thanks colleagues for
tracking down shoplifting suspect Update:
North Olmsted, OH: Police Officer hit by fleeing car thanks colleagues for
tracking down shoplifting suspect
Seattle, WA: Man shoplifts, stabs employee in leg, tracked down by K-9 in
Seattle
Oklahoma City, OK: Shoplifting suspect assaults loss prevention officer at
Kohl's
Kingston, ON, CN: Walmart store security officer assaulted, threatened with
knife
Owasso, OK: Lowe's Shoplifter leads Police on high-speed chase into Tulsa
Bismarck, ND: Restaurant Employee charged with stealing $50,000 from employer,
gambling it away
Scarsdale, AZ: Woman Uses Stolen Credit Card Info to Fraudulently Purchase $1K
Gibson Guitar; tied to several other transactions
Mesa, AZ: Man arrested after stealing electric shopping cart, merchandise at
Safeway
Akron, OH: Police ID suspect in string of robberies; Walgreens, CVS, Family
Dollar and Little Caesars
|
|
&uuid=(email))
|
| |
|
&uuid=(email))
|
 |
|
|
Daily Totals:
• 21 robberies
• 3 burglaries
• 0 shootings
• 0 killed |
|
|
Click to enlarge map
|
&uuid=(email))
|
|
|
 |
|
 |
|
Submit Your New Hires/Promotions or New Position
|
|
|
|
&uuid=(email)) |
|
|
|
&uuid=(email))

|
|
|
Featured Job Spotlights
NEW
 |
Regional Asset Protection Manager (Southeast)
Florida/Georgia (Home-based,
must reside in the SE)
The successful candidate will be responsible for the management of the Asset
Protection function in their assigned area. Guide the implementation and
training of Asset Protection programs, enforcement of policies and procedures,
auditing, investigations and directing of shrink reduction efforts...
|

|
Profit Protection Leader
Corte Madera, CA
Responsible for leading and execution of the Protection and Prevention tiers of
the Profit Protection strategy for all RH locations including our Corporate
Campus in Corte Madera, CA - PROTECTION - Access Control | Alarms | CCTV |
Guards - PREVENTION - Awareness | Audits | P&P | Training...
|

|
Loss
Prevention Manager
Las Vegas, NV
● Demonstrate management leadership skill to achieve the goals of the
Company.
● Experienced with and has knowledge of regulatory agencies to include:
TSA, DOT and OSHA.
● Establishes and communicates a risk business plan consistent with the
objectives of the Company that pro-actively identifies and corrects poor
behaviors...
|
 |
Field Loss Prevention Manager
Oklahoma City, OK
As a Retail Loss Prevention Manager for Staples, you will manage and coordinate
Loss Prevention and Safety Programs intended to protect Staples assets and
ensure a safe work environment within Staples Retail locations...
|
 |
Risk Management and Asset Protection Manager
Kansas City, MO
This role is responsible for risk management, physical security, and loss
prevention in Hallmark Gold Crown retail stores and will monitor internal and
external theft, consumer and retailer fraud, and employee and consumer
injuries...
|

|
Region Asset Protection Manager
Jacksonville, FL
Responsible for managing asset protection programs designed to minimize shrink,
associate and customer liability accidents, bad check and cash loss, and safety
incidents for stores within assigned region. This position will develop the
framework for the groups' response to critical incidents, investigative needs,
safety concerns and regulatory agency visits...
|
Featured Jobs
To apply to any of today's Featured Jobs,
Click Here
|
|
View Featured
Jobs |
Post Your Job
|
|
&uuid=(email))
|
|
|
|
|
|
|
|

&uuid=(email)) |
|
|
Hearing what they say goes well beyond the words. Hearing what they don't say is
an art that sometimes turns into a dog bite.
Just a Thought,
Gus

 |
|
We want to post your tips or advice... Click here |
|
&uuid=(email))
|
|
|
|
Not getting the Daily? Is it ending up in your spam folder?
Please make sure to add d-ddaily@downing-downing.com to your contact list,
address book, trusted sender list, and/or company whitelist to ensure you
receive our newsletter.
Want to know how?
Read Here |
|
|
|
 |

&uuid=(email))
&uuid=(email))
&uuid=(email))


&uuid=(email))
&uuid=(email))
&uuid=(email))



&uuid=(email))
&uuid=(email))
&uuid=(email))

&uuid=(email))
&uuid=(email))
&uuid=(email))

&uuid=(email))


&uuid=(email))
&uuid=(email))
&uuid=(email))

&uuid=(email))
&uuid=(email))

&uuid=(email))
&uuid=(email))
&uuid=(email))
&uuid=(email))







%20V2.png)











&uuid=(email))












&uuid=(email))




 U.S.
health officials issued what appears to be a strong warning about novel
coronavirus on Tuesday - it is not a matter of if, but when it will spread in
communities in the U.S. and that Americans should prepare for "significant
disruption" to their lives as a result of the virus.
U.S.
health officials issued what appears to be a strong warning about novel
coronavirus on Tuesday - it is not a matter of if, but when it will spread in
communities in the U.S. and that Americans should prepare for "significant
disruption" to their lives as a result of the virus.





&uuid=(email))











&uuid=(email))

&uuid=(email))

 By
Tony Gallo, Managing Partner & Katharine Baxter,
Lead Technical Writer for Sapphire Risk Advisory Group
By
Tony Gallo, Managing Partner & Katharine Baxter,
Lead Technical Writer for Sapphire Risk Advisory Group An
emphasis on cannabis for medical purposes also became popular throughout the
Roman Empire by the Common Era. Roman medical texts from this period explain the
plant's use for external wounds, tumors, abdominal pain, and inflammation.
Writings also depict cannabis' use recreationally as an intoxicant in the
ancient Roman culture.
An
emphasis on cannabis for medical purposes also became popular throughout the
Roman Empire by the Common Era. Roman medical texts from this period explain the
plant's use for external wounds, tumors, abdominal pain, and inflammation.
Writings also depict cannabis' use recreationally as an intoxicant in the
ancient Roman culture.&uuid=(email))
&uuid=(email))

&uuid=(email))

&uuid=(email))
&uuid=(email))
&uuid=(email))
&uuid=(email))
&uuid=(email))



&uuid=(email))
&uuid=(email))


&uuid=(email))

&uuid=(email))
&uuid=(email))







&uuid=(email))


&uuid=(email))

&uuid=(email))
