|
|





.jpg)







.jpg)

|

|

|

"Your full service
physical security team"

Each number on a team member's jersey represents the year they joined the
company
Front row, left to right:
Bill Crowley, Sean Siegel, Pete Sutton, Duane House, Tom Capranica, Holly
Morrison, Steve Hornbeck, Jennifer Graves, Danielle Hoover, Chrissy Miller,
Nikki Mobley, Karen Angeles, Julie Wallace, Lili Granger, Chad Kennedy, Tony
Kates
Second row, left to right:
Dan Israel, Nate Wetmore, Rebecca Boresow, Christian Turner, Matt Brown, Natalie
Kimbrell, Cathy Campbell, Heather Benker
Third row, left to right:
Keith Padgett, Don Stroh, David Israel, Phil Michael, Rob Wright, Matt Setter,
Doug Taylor, John Kupka, Mark Barrett, Mike McCluskey, Ed McCampbell, Brandi
Dameron, Jason Hamlin, Sergio Meraz, Stacy Derks, Jacque Britton, Natasha
Woodley
Submit Your Group LP Selfie and Group Vendor
Selfies Today!

|

|

|
CA Prop 47 Impact - Brought to
you by ALTO Alliance
"Rainbow Crews" Theft On the Rise in The Bay
Uptick in San Francisco retail theft
 Retail
theft is on the uptick in San Francisco, and while luxury goods were once the
focus, now it seems as if those stealing are going for lower end merchandise. Retail
theft is on the uptick in San Francisco, and while luxury goods were once the
focus, now it seems as if those stealing are going for lower end merchandise.
Police confirm retail theft is on the uptick specifically in parts of North
Beach, Fisherman's Wharf, and Union Square.
While luxury goods were once the prime target, groups of people are now
expanding to drug stores.
Viewer video sent to KRON4
shows a robbery at the Walgreens on Columbus and Bay streets last week. But
it's not just Walgreens.
 The
CVS Pharmacy at Stockton and Sutter was hit back in June. People are seen taking
what they want with apparently no care in the world. The
CVS Pharmacy at Stockton and Sutter was hit back in June. People are seen taking
what they want with apparently no care in the world.
And there is a video of another robbery at the same store this weekend. Once
again, people are seen rifling through merchandise and sticking it in their bag
before heading out the door.
A spokesman for CVS says it takes the matter of organized retail crime seriously
and it partners with law enforcement and other retailers with a goal of
preventing this activity and bringing to justice those responsible for it.
So far, there have been no arrests in the drug store robberies, nor any
indication that those involved are connected, but police say there appears to
be a lot of teenagers involved in the recent uptick in these types of crimes.
kron4.com
ISCPO's Executive Roundtable Interview Series
John Cannon, Special Agent in Charge of the GBI Major Theft Unit
 As
part of our Executive Roundtable Interview Series, we sat down with
prominent law enforcement veteran John Cannon, Special Agent in Charge
(SAC) of the GBI Major Theft Unit with the Georgia Bureau of
Investigation (GBI). An active ISCPO board member, he provides a unique
perspective when it comes to setting best practices in conducting major
theft investigations. We asked him to share his take on where the
industry is going in combating crime and how LP practitioners can
effectively work with law enforcement to mitigate loss. As
part of our Executive Roundtable Interview Series, we sat down with
prominent law enforcement veteran John Cannon, Special Agent in Charge
(SAC) of the GBI Major Theft Unit with the Georgia Bureau of
Investigation (GBI). An active ISCPO board member, he provides a unique
perspective when it comes to setting best practices in conducting major
theft investigations. We asked him to share his take on where the
industry is going in combating crime and how LP practitioners can
effectively work with law enforcement to mitigate loss.
ISCPO: How has the industry evolved since you started out,
especially related to how technology aids in investigations?
I think the use of technology has increased, especially with high value
loads. When tracking devices are utilized by the transportation industry
and used correctly, it provides us with a greater opportunity to recover
a stolen load. Real time monitoring and timely notification improves the
chance of making a full recovery. As with any organized criminals who
adjust to investigative techniques, cargo thieves have responded to the
use of technology utilized by the transportation industry. On the
flip-side. we have seen an increase in the use of GPS jamming devices
being used by the organized cargo theft groups, especially the groups
from South Florida.
ISCPO: In your experience, how can Public Sector & Law Enforcement
can work together with Private Sector better?

Prior to my assignment regarding cargo theft, I spent most of my career
in drug enforcement with the GBI. Initially it was difficult for me to
understand the concept of sharing information with the private sector. I
quickly realized the importance and benefit of working together with
private sector investigators. While it may sound easy, it takes time to
develop that level of trust to share information.
Read the full interview here
Editor's Note: There's been a number of articles testifying to the
success of the GBI since its inception a few years ago and the dramatic impact
it's had on reducing cargo theft. A well-deserved article and call out.
CargoNet's Second Quarter 2018 Cargo Theft Trend
Analysis
California & Florida Top Almost Every List
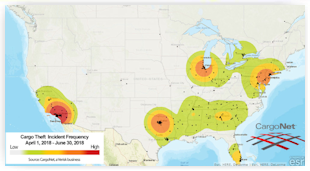 In
the second quarter of 2018, CargoNet recorded 328 supply chain risk
intelligence events in the United States and Canada. Sixty-four percent of
incidents involved a stolen vehicle, and 48% involved stolen cargo among several
other kinds of events, such as identity theft, missing drivers, and police
intelligence. In total, CargoNet recorded 157 cargo thefts across the United
States and Canada in second-quarter 2018, a 4% decrease from second-quarter
2017. The average cargo value per theft event was $186,779, for a total
estimated loss of $29.3 million across the United States and Canada in this
analysis period. There were 342 stolen vehicles recorded, including 120
semi-tractors and 155 semi-trailers. In
the second quarter of 2018, CargoNet recorded 328 supply chain risk
intelligence events in the United States and Canada. Sixty-four percent of
incidents involved a stolen vehicle, and 48% involved stolen cargo among several
other kinds of events, such as identity theft, missing drivers, and police
intelligence. In total, CargoNet recorded 157 cargo thefts across the United
States and Canada in second-quarter 2018, a 4% decrease from second-quarter
2017. The average cargo value per theft event was $186,779, for a total
estimated loss of $29.3 million across the United States and Canada in this
analysis period. There were 342 stolen vehicles recorded, including 120
semi-tractors and 155 semi-trailers.
California reported 34 cargo thefts in second-quarter 2018; thefts in the state
were down 21% from second-quarter 2017. Florida was a distant second place, with
22 reported cargo thefts. CargoNet also recorded an increase in cargo theft in
the province of Ontario and the state of Illinois. We also note that one of the
top states for cargo theft, New Jersey, continued a downward trend in theft.
ajot.com
Sports Apparel Giant Fanatics Sued for Racial Discrimination
The U.S. government is suing Fanatics Inc., the sports apparel company whose
investors include the National Football League and Major League Baseball, for
racial discrimination, harassment and retaliation.
Filed Tuesday in district court in Florida, the
suit brought by the U.S. Equal Employment Opportunity Commission centers
mainly around claims by a former employee, a black man, who says he was
repeatedly subjected to discrimination during his time at the company's
Jacksonville headquarters.
The accusations include a team leader using the n-word on the employee's first
day of work, and other comments from colleagues and superiors such as "I'm not
racist but a lot of you [black] guys can't read" and "Africans in Europe know
their place, but not in the United States."
Other Fanatics employees describe the workplace as racially divided, with
separate treatment of white and black employees, according the lawsuit. A former
Operations Administrator said minorities are "treated like uneducated slave
labor."
"Fanatics is committed to treating all employees fairly and takes complaints
like this very seriously," the company said in a statement. "We deny any
wrongdoing and look forward to vigorously defending these claims in court."
bloomberg.com
No other state witnessed as many Identity Fraud
reports per capita as Florida throughout 2017
Residents of Florida, Michigan and Nevada are among the most likely in the U.S.
to report being targeted by fraudsters and identity thieves, according to a
report from the Federal Trade Commission. The FTC's Consumer Sentinel Network
recorded roughly 1.1 million reports of fraud in 2017 - with scammers posing as
government officials, distant relatives and technical support staff in a bid to
trick consumers into paying them. Consumers reported being tricked out of more
than $900 million last year, up more than $60 million from their losses in 2016.
usnews.com
'Security Guard By Day - Homeless By Night'
London, UK: Tens of thousands of people are working for high street brands while
homeless because they can't afford a roof over their head
Set on London's exclusive Bond Street, the Prada boutique attracts a crowd of
wealthy patrons spending thousands of pounds on designer clothes and handbags.
Yet for the store's security guard, Kallum, this glamorous world lies in stark
contrast to his life outside work. As the store's shutters close, Kallum has no
home to return to, and instead sleeps rough on the capital's streets. Even more
shockingly, his case is not unique.
Channel 4's Dispatches programme, aired on Monday night, will reveal tens of
thousands of people - some working for the nation's most recognisable high
street brands - are sleeping rough because they cannot afford a roof over their
heads.
dailymail.co.uk
Four predictions on how retailing will evolve
The retailers who flourish in the upcoming years will be those that re-imagine
and align their stores with the digital age.
• End of long-checkout queues: Saying goodbye to long checkout lines will
be one of the most well-known retail trends that will go mainstream in the next
few years. The future of retail will look more hopeful than ever before by
helping consumers dodge queues and offering customers with a hassle-free
shopping experience.
 • Embracing the Millennial mentality: The future of the retail industry
will significantly revolve around the preferences and tastes of Millennials.
Millennials usually tend to be more loyal to brands that stand for the right
values, like authenticity, transparency, and social responsibility. Transparency
is one of the retail trends that will soon become a fixed factor in the retail
industry. • Embracing the Millennial mentality: The future of the retail industry
will significantly revolve around the preferences and tastes of Millennials.
Millennials usually tend to be more loyal to brands that stand for the right
values, like authenticity, transparency, and social responsibility. Transparency
is one of the retail trends that will soon become a fixed factor in the retail
industry.
• Stores that recognize customers: The brick-and- mortar retailers are
inspired by online retailers to know their customers better. This means that we
can soon expect physical stores to find customers in the aisles via facial
recognition or biometrics and save their browsing and purchase history
immediately.
• More small format stores: Small format stores will be a prominent trend
in the future of retail. Many retailers are taking an inverse approach to
surviving by becoming small and nimble rather than trying to compete with online
stores' large catalog and endless aisles.
To view a comprehensive list of the factors affecting the future of the retail
industry,
click here.
chainstoreage.com
Oracle Retail Breaks Down Inventory Barriers with
Cloud Service
To empower retailers to more easily track, access and manage inventory in store
Oracle Retail has introduced a new
Store Inventory Operations Cloud Service. By providing the ability to view
inventory by size, color and other key attributes, the Oracle Retail Cloud
Service helps retailers improve customer satisfaction and fulfill demand
regardless of channel.
prnewswirecom
How to Have the Termination Discussion
What to say and what not to say when separating an employee for cause
Termination meetings are always challenging. Minutes before you call the
employee into your office, your heart pounds; you experience mixed emotions of
guilt, fear and justification; and you mentally rehearse what to say and how to
say it.
When a breach of progressive disciplinary warnings results in a termination for
cause due to poor performance, you have choices: keep the individual at arm's
length throughout the discussion; create a threatening and intimidating
atmosphere to persuade the individual not to sue you; or extend an olive branch
and help the individual come to terms with this new reality, heal the wound, and
get on with his or her life.
shrm.org
Vice President Loss Prevention position posted at
Fred's Inc., Memphis, TN
The Vice President Loss Prevention is responsible for providing direction,
development and leadership to Loss Prevention, Safety, Security and Audit teams
for corporate, distribution centers and the field. These teams directly impact
enterprise shortage control, security awareness, and program compliance for all
Fred's retail locations. The Vice President manages multiple Security, Loss
Prevention and Safety programs and initiatives for stores and in our corporate
offices.
jobs.net
Fred's, Inc. operates approximately 600 general merchandise and pharmacy stores,
including 13 franchised locations.
Director, Risk Management and Safety job posted
at Guess, Los Angeles, CA
An anti-Trump boycott ending its crusade against
24 companies that sell Ivanka Trump products
Giant Eagle offers Scan Pay & Go 'as-you-shop'
option at 3 central Ohio stores
Quarterly Results
LVMH Q2 revenue up 11%, first half yr. revenue up 10%

|
|
|
All the News - One
Place - One Source - One Time
The D&D Daily respects your time & doesn't
filter retail's reality
|
|

|
 |
 |

|

|
|
P.O.P.
Security Invisi-Shield® System

Are you looking for a simple yet effective solution to secure products and
reduce shrink? The innovative and easy-to-use P.O.P. Security Invisi-Shield®
System from FFR Merchandising, a siffron company, can help you do just that.
This open (not under lock and key) loss prevention system secures high-value,
high-theft product while allowing customer access to the product for purchase.
The
P.O.P.
Security Invisi-Shield System features clear "invisible" panels that
control inventory while providing an unobstructed view of consumer product.
Panels slide along a rail to allow single product access for legitimate
customers while preventing "shelf sweeping" theft. As customer slides panel to
access product, a manual clicking sound alerts store personnel to activity.
Available for narrow, wide, or tall products, the panels feature contoured edges
that are intuitive and comfortable for shopping.
The plastic panels are nearly unbreakable, even in high-traffic environments,
and have been designed to install easily on perforated gondola shelves with
minimal to no impact on existing planogram. Optional accessories, such as
locking panel, end panels, and security bar cover, provide additional security
by further limiting access to the product.
 To provide greater protection from shelf sweeping, reduced labor and improved
organization, use with any of our Power Zone® Self-facing Systems. To provide greater protection from shelf sweeping, reduced labor and improved
organization, use with any of our Power Zone® Self-facing Systems.
To see how it works, check out the
video here.
For more information on the P.O.P. Security Invisi-Shield System and how it
works, contact FFR Merchandising at 800.422.2547 or visit
www.ffr.com. |

|
_2.jpg) |

|

|
|
A MUST Read
The Most Revealing Study We've Reported On
72% of CEOs Steal Corporate IP from Former Employers
Higher security budgets and advanced new tech won't protect your data from a CEO
who decides to bring it outside the enterprise - and it turns out many have a
habit of doing just that.
There remains a great disparity between how business leaders claim to approach
cybersecurity and how they act, researchers found in Code42's 2018 Data Exposure
Report, which surveyed 1,034 security and IT leaders (CSOs, CTOs, CISOs, CIOs)
and 600 CEOs and business leaders.
Most (78% of) CEOs and 74% of business leaders say intellectual property (IP) is
the most valuable asset in the enterprise; however, 72% of CEOs admit to
taking IP from a past employer. Nearly half of business leaders and 71%
of CMOs claim to have done the same thing.
"I think we all know when people leave companies they take information with
them," says Code42 CISO Jadee Hanson. "The startling stat in here is the
amount the C-suite executive level answered and said, 'Yes, I take information
when I leave a company.'"
The security side is concerned: 78% of CISOs polled say greatest risk to
organizations is people who disregard policies and rules to do their jobs the
way they want. But it's tricky to convince employees to change dangerous habits
when many don't think they're doing anything wrong.
Three-quarters of CEOs say "it's not just corporate data, it's my work, my
ideas." Seventy percent of business leaders agree. Both CEOs and businesses
leaders feel ownership because, as they state, they "impart" themselves into
their work and it should be considered theirs. Nearly all (93% of) CEOs keep a
copy of their work on a personal device or storage account.
"People don't even think of it as stealing information and taking it with
them," says Hanson.
You Can Click, But You Can't Hide
Half of business leaders and 63% of CEOs admit they've clicked links when
they didn't mean to or thought they shouldn't have. As a result, 34% of CEOS
had to change their passwords, one-quarter lost control of their accounts and
25% paid ransomware,
researchers report.
14% of CEOs and 36% of business leaders don't report these incidents because
they thought they could sort it out themselves (36% and 38%), didn't think it
posed a security risk (20% and 24%), feared the repercussions (26% and 23%), or
"hoped nothing would happen" (27% and 22%).
Think Before You Download
Nearly 60% of CEOs admit to downloading software without knowing whether it's
security-approved, which marks a decline from 75% in 2017 but still
signifies a major problem. Of the CEOs who download unapproved software, 77%
think it would be considered a security risk.
It's not only leadership who's going behind security's back: 70% of CISOs and
62% of IT and security leaders believe all employees are downloading unapproved
software. The reasons are varied; employees claim they use unapproved apps
because they use the same tools in their personal life, those apps make things
easier, or the company-provided software isn't as good.
darkreading.com
Editor's Note: Don't Shoot The Messenger
So how does Corporate America and more importantly the CSO's and LP/AP senior
leaders deal with this? Is it a matter for the Board's Audit Committee? Does the
Board of Directors discuss this and who presents this study to them?
In this new age of total transparency, as mentioned above in an article/study
about retail survival, and as evidenced around the country with all of the
senior management departures involving miss-conduct obviously it needs to be
addressed. Because as AI develops and is integrated more and more this will come
to the surface and present some interesting dilemma's for senior leadership and
boards.
It will ultimately end up as a contractual obligation which for the most part
already exists. The issue is do the boards enforce it, are they even looking at
it and once again who presents it? Because in the real world they do shoot the
messenger. Just a thought. Gus Downing
IBM Study: Cost of a Data Breach Reaches $350 Million
A study sponsored by IBM Security and conducted by Ponemon Institute found that
the average cost of a data breach globally is $3.86 million, a 6.4
percent increase from the 2017 report.
This year for the first time, the
2018 Cost of a Data Breach Study also calculated the costs associated with
"mega breaches" ranging from 1 million to 50 million records lost, projecting
that these breaches cost companies between $40 million and $350 million
respectively.
"While highly publicized data breaches often report losses in the millions,
these numbers are highly variable and often focused on a few specific costs
which are easily quantified," said Wendi Whitmore, Global Lead for IBM X-Force
Incident Response and Intelligence Services (IRIS). "The truth is there are many
hidden expenses which must be taken into account, such as reputational damage,
customer turnover and operational costs. Knowing where the costs lie, and how to
reduce them, can help companies invest their resources more strategically and
lower the huge financial risks at stake."
Key findings include:
● Average cost of a data breach of 1 million compromised records is nearly $40
million
● At 50 million records, estimated total cost of a breach is $350 million
● The vast majority of these breaches (10 out of 11) stemmed from malicious and
criminal attacks (as opposed to system glitches or human error)
● The average time to detect and contain a mega breach was 365 days - almost 100
days longer than a smaller scale breach (266 days)
securitymagazine.com
Business Email Scams Spin Even Wider Webs
Attackers will target the payment method you most commonly use
If the Business Email Compromise (BEC) scam isn't on the radar of every
corporate finance executive, it certainly should be. The Federal Bureau of
Investigation (FBI) recently issued a public service announcement warning that
the BEC scam has now redirected $12 billion worldwide, much of that now having
to be written off as a loss for corporates unable to recover the funds.
A new report finds fraudsters are spinning their BEC webs even broader,
targeting new channels of business transactions.
More than three quarters of companies became targets of payments fraud last
year, yet another all-time high. While the continued strength of BEC scammers
may not come as a surprise, the research finds that the scam no longer only
reigns in targets with a request for wire transfer. Of the businesses that have
been hit by a scam, 77 percent were the target of a BEC scam, the report said.
While 54 percent of those scams involved wire transfers, more than a third
targeted check payments.
According to the AFP, an attacker will target the payment rail that is most
commonly used by the victim to pay suppliers, thus, limiting suspicions.
This means that, though ACH payments have developed a reputation of greater
security compared with checks, BEC scammers are also committing the scam to
request fraudulent ACH transfers, too. Of respondents who said they were
targeted by payments fraud last year, a combined 41 percent said the fraud
involved ACH transactions, both debit and credit.
pymnts.com
You might not always stop the hackers
But you can make sure you bounce back faster after an attack
Murphy's Law: Anything that can go wrong
will go wrong
 What's the biggest problem with most existing approaches to internet security?
Many would say that it only guards effectively against known, easily-identified
threats, and takes too long to respond to new ones. Hackers are nothing if not
inventive when it comes to finding and exploiting new 'zero day' threats,
whether in applications, operating systems or the software infrastructure that
underpins websites and services. They're attacking vulnerable endpoints and
using them to move laterally across to other systems. They're attacking
third-party suppliers or exploiting the weaknesses of employees to find a way
into the network. They're finding modes of attack that don't get caught by
traditional anti-malware tools. What's the biggest problem with most existing approaches to internet security?
Many would say that it only guards effectively against known, easily-identified
threats, and takes too long to respond to new ones. Hackers are nothing if not
inventive when it comes to finding and exploiting new 'zero day' threats,
whether in applications, operating systems or the software infrastructure that
underpins websites and services. They're attacking vulnerable endpoints and
using them to move laterally across to other systems. They're attacking
third-party suppliers or exploiting the weaknesses of employees to find a way
into the network. They're finding modes of attack that don't get caught by
traditional anti-malware tools.
That's why the focus on protection and protection alone is not enough to protect
enterprises and their data. Instead, businesses need to adopt a more balanced
strategy; one that backs up protection with resilience. This isn't about
lowering your perimeter walls and opening the gates, but accepting that,
eventually, some attempts will make it over or through, and having systems in
place to deal quickly with any threats and minimise their impact.
Leading security researchers have understood this for some time. As Simon Schiu
and Boris Balacheff of HP's Security Labs wrote at the end of 2016: "The
security profession is finally accepting this axiom: given enough resources, an
attacker will eventually be successful. This means designing not only security
protections, but also mechanisms that detect when protections fail and help
recover devices or infrastructure to a good state, at both machine speed and at
scale."
itpro.co.uk
5 Steps for Better Data Protection & Privacy
1. Get to know your own data - Can you identify exactly where all of your
organisation's personal data is being held? If not, you need to map out all of
your systems to find out. The best way to do this is to track the path of the
data from the moment it first enters your organisation, be it physically or
digitally. From here, establish where it has ended up and where it has been in
the process.
2. Less is more - One excellent recommendation of the EU GDPR is to hold
as little personal data as possible. The more information you have, the more
attractive you are to hackers and the more you have to lose. Our own advice is
to assume that you will certainly be breached at some point and to minimise the
damage when that happens. Ideally, when the hacker breaks in they will find
nothing of value.
3. Make life harder for hackers - If you do need to keep personal data,
put as many obstacles as possible in the way of the fraudster. Use tokenisation
or pseudonymisation and separate uniquely identifiable details such as email
addresses and telephone numbers from all other data. In this way, complete
records are assembled only when a record is actively required for the purposes
of a specific transaction or query.
4. Educate your employees - A recent study by HANDD Business Solutions
has found that employees are frequently a business's weakest link when it comes
to data protection. While it's important to trust your staff, regular training
in basic security procedures such as changing passwords and looking out for
phishing or spear phishing attacks is absolutely essential. Managers must ensure
that policies are kept up to date and hold regular tests to make sure that the
entire team knows how to put these into action.
5. It's not just about you - Making sure the customer data that you hold
is secure and encrypted is only the first hurdle. If you are working with
partners for some aspects of data processing, then it's up to you to make sure
that their processes and security measures are as robust as yours.
information-age.com
Threat Hunting: Rethinking 'Needle in a Haystack'
Security Defenses
Business executives are finally getting the message from IT and security leaders
that they need to be more proactive when it comes to cybersecurity. They can't
afford to let their cybersecurity teams wait for alerts that may come too late
to stop a minor intrusion from becoming a major breach. Threat hunting is the
approach business leaders need to detect these incidents early enough to stop
them.
Where leadership holds both authority and responsibility for these functions,
they may not know enough about threat hunting to provide much-needed direction.
It's often up to frontline defenders to figure out how to get that initiative on
stable footing.
At any organization, the sheer number of "events" to sort through can make early
detection daunting. It's easy to reach for the "needle in a haystack" metaphor,
but this is a flawed perception of the problem. The old saying assumes that you
know there is a needle, that you know what a needle looks like, and that it is
in fact a needle you're looking for. This doesn't address the fact that, in the
cyber world, needles (that is, threats) can disappear quickly for a wide variety
of reasons - and often long after the malicious party has completed what he or
she came to do.
Although there are many factors for cybersecurity teams to juggle, getting
started isn't hard. Read on.
darkreading.com
BEC Scammer Gets 4 Yrs Prison - Hitting Seven
Companies in U.S. & Abroad
for $900K
Emeka Ndukwu, 46, of Upper Marlboro, Md. a dual citizen of the United States and
Nigeria, was sentenced today to four years in prison for conspiring to launder
the proceeds of scams that tricked seven companies in the United States and
abroad into wiring more than $900,000 into accounts controlled by various
co-conspirators. Business e-mail ("BEC") compromise schemes; typically a
co-conspirator tricks a company into transferring large sums of money into
accounts controlled by others participating in the scheme.
justice.gov
|
 |
|

|
|

|
|

Canada becomes second nation in the world to legalize marijuana
"Keeping Profits Out of the Hand of Criminals & Organized Crime"
Canada is only the second country in the world -- and the first G7
nation -- to implement legislation to permit a nationwide marijuana
market. In the neighboring US, nine states and the District of
Columbia now allow for recreational marijuana use, and 30 allow for
medical use. Uruguay was the first country to
legalize marijuana's production, sale and consumption in
December 2013.
Bill C-45, otherwise known as the Cannabis Act, stems from a
campaign pledge of Prime Minister Justin Trudeau to keep marijuana
away from underage users and reduce related crime.
Although the Canadian government had initially stated its intent to
implement by July 2018, provinces and territories, who will be
responsible for drafting their own rules for marijuana sales, have
advised that they would need eight to 12 weeks after the Senate
approval to transition to the new framework.
On June 19, 2018 Justin Trudeau tweeted:
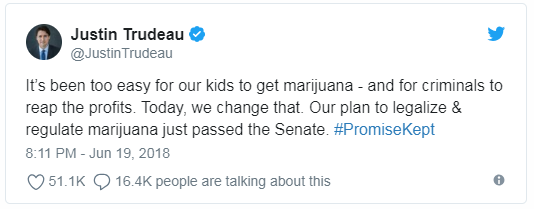
"This is an historic milestone for progressive policy in Canada,"
she tweeted. "This legislation will help protect our youth from
the risks of cannabis while keeping profits out of the hands of
criminals and organized crime."
Once the
bill is formally approved, adults will be able to carry and
share up to 30 grams of legal marijuana in public. They also will be
allowed to cultivate up to four plants in their households and
prepare products such as edibles for personal use.
However, stringent rules will still govern the purchase and use of
marijuana.
Consumers are expected to purchase marijuana from retailers
regulated by provinces, territories or -- when neither of those
options are available -- federally licensed producers. Marijuana
will also not be sold in the same location as alcohol or tobacco.
The Canadian government has also implemented changes to their
impaired driving laws, to address repercussions for driving
under the influence of cannabis.
The bill set a floor on the minimum age of the consumer at 18 years,
and makes the production, distribution, or sale of cannabis products
an offense for minors.
 Market Boom Market Boom
C-45 is also expected to spark a billion-dollar industry, given
total spending on marijuana could
surge as high as 58%, especially as users are expected to be
willing to pay a premium for legal access to the drug.
In the United States, BDS Analytics estimated that the pot industry
took in nearly $9 billion in sales in 2017. The revenue from the
sales is equivalent to the entire snack bar industry.
As provinces decide local rules of implementation, marijuana
availability will vary across the country. In Alberta, recreational
weed will be widely available at more than 200 private retailers
across the province. On the opposite end of the spectrum,
marijuana availability will only be provided in 40 state-run
shops in Ontario. In Newfoundland and Labrador, it will be available
in Loblaws grocery stores.
cnn.com
Upcoming Cannabis Legalization is
Dominating All Canadian News
RCC Plans Half Day Special Loss Prevention Conference
 From Provinces struggling with licenses, locations, amounts,
organized crime, and security. Not a day goes by without articles
appearing across Canada. Even the Retail Council of Canada is
planning a
special half day session at their upcoming Loss
Prevention conference devoted to the subject. From Provinces struggling with licenses, locations, amounts,
organized crime, and security. Not a day goes by without articles
appearing across Canada. Even the Retail Council of Canada is
planning a
special half day session at their upcoming Loss
Prevention conference devoted to the subject.
This is the precursor for the states as the U.S. trend continues as
Canada will be the subject matter experts going forward. As
mainstream retail will be involved or at least impacted in some form
sooner or later. -Gus Downing
LP & Security Impact
Legalization of cannabis a groundswell of opportunity for security providers
 "This is a huge business opportunity," says David Hyde, when asked how the
upcoming legalization of recreational cannabis under The Cannabis Act will
impact the security business. "This is a huge business opportunity," says David Hyde, when asked how the
upcoming legalization of recreational cannabis under The Cannabis Act will
impact the security business.
Hyde, owner and principal consultant at David Hyde and Associates, a risk
management and security services consultancy based in Toronto, is not alone in
this belief. Even prior to legalization, companies and consultants have seen
opportunities to expand their business under the ACMPR, or the Access to
Cannabis for Medical Purposes Regulation.
Expanding growth opportunities
Despite the difficulties of entering a new, somewhat "unconventional" industry,
there is plenty of evidence to indicate the cannabis market will provide
opportunities for growth.
"Within a six-month span, we have grown from just under 20 staff to more than
100 Canada-wide, and we project that we will exceed 200 by the fall of this
year," says the owner of 3Sixty Secure.
Retail = revenue
For security service providers looking to enter the market, Hyde says he
believes there are plenty of new opportunities. Today, there are 90
cultivation sites that are federally regulated, he says, and this will
grow to 150 by mid-summer. Each of these sites will need security systems
and guards.
Regulatory gaps
Part of doing your homework includes being aware of regulatory gaps that
impact security, particularly transportation security. In fact, under the
ACMPR, there are no regulations regarding the transportation of medical
cannabis. As a result, the industry, particularly providers of secure
transportation services, are setting their own security standards.
Holistic security
To capitalize on the cannabis market, not only is it important to be aware of
regulatory gaps, but also of the strict physical security regulations under the
ACMPR. The ACMPR focuses on barriers, doors, gates, ceilings and other
aspects of the physical security of cannabis facilities. It is also focused on
technological security and systems, including cameras, access control,
intrusion, and more, explains Hyde.
canadiansecuritymag.com
Security policies and legal marijuana
With legal recreational cannabis coming to Canada next year,
security professionals may be faced with new questions. Experts and
consultants provide an update on the current legal status and what
we can expect in 2018.
canadiansecuritymag.com
Read the full report here
More Canadian News
Free Webinar on July 26 - Tomorrow!
Active Threats: Are You prepared?
An integrated-rescue system for mass-casualty incident prep
Join Canadian
Security, Blue
Line and
Fire Fighting in
Canada on July 26 at 2 pm EST for an exclusive and free webinar on first
responders preparing together for active threats.
The recent van attack in Toronto, the 2014 shooting of a reserve army corporal
in Ottawa and the 2017 Quebec City mosque shooting are several examples of why
efficient emergency response to crisis situations is top of mind.
gotowebinar.com
Nominations for 2018 Security Director of the Year close July 27
The Security Director of the Year award, sponsored by Anixter Canada, is awarded
each fall to a senior security director or manager working in an end user
environment who has demonstrated leadership and achievement in the industry. The
winner is chosen by Canadian Security magazine's Editorial Advisory Board from
the nominations submitted. The judges consider a number of factors, including a
major project or initiative completed in the last year, their contribution to
the industry and their commitment to furthering the professionalism of the
industry. Deadline for entries is July 27, 2018.
surveymonkey.com
|
RCC Retail Secure 2018 - September 20
 RCC
Retail Secure is Retail Council of Canada's newly expanded loss
prevention conference designed for retailers. This all-day event
will explore three significant issues in the changing reality of
retail: Fraud Protection, Data Security and Loss Prevention. RCC
Retail Secure is Retail Council of Canada's newly expanded loss
prevention conference designed for retailers. This all-day event
will explore three significant issues in the changing reality of
retail: Fraud Protection, Data Security and Loss Prevention.
To provide depth on these issues, specialized educational sessions
have been developed for attendees to customize their learning
experience during the conference. Leading security, protection and
prevention experts will present best practices and improvement
strategies. This event will also feature a full range of exhibitors
to provide expertise on the latest in asset protection programs,
technology and investigation techniques.
Register for Retail Secure 2018 today
View the agenda |
|
|

|
|
 |
|

|
|

|
|
Critical Incident Management - Technology - Response
Pat McEvoy,
Sr. Dir of AP Administration, Hudson's Bay Company
Bryan Granata, Managing
Dir of AP,
Saks Fifth Avenue
|

|
With lone wolf terrorist attacks happening more frequently in the greater NYC
area and active shooter incidents increasing nationwide, the need for critical
incident management programs, technology and hardware has never been more
important.
Pat McEvoy, Sr. Director of Asset Protection Administration, Hudson's Bay
Company and Bryan Granata, Managing Director of Asset Protection, Saks
Fifth Avenue, tell us about the preventative measures their stores are taking
from training drills and K9 dogs to gunshot detection systems. |
Episode Sponsored By

|
|

|
|
 |
|

|
|
 |
|

|
|

|
|
Artificial Intelligence Is Being Used to
Combat Luxury Fakes
Entrupy, Goat use AI to find counterfeit handbags and sneakers
In 2017, US Customs seized
more than 34,000 shipments of counterfeit goods, an 8 percent increase
from 2016. Retailers are scrambling to get ahead of the counterfeiters and
have begun to explore how technology can help.
Artificial intelligence has increased the arsenal of tools at their
disposal, but AI can be costly to implement. Still, the demand is growing,
and a few companies have stopped relying solely on human expertise.
Goat and Entrupy are two very different companies that have developed
anti-counterfeit algorithms based on immense databases of information on top
luxury brands. They use these databases to look for the tiniest of
inconsistencies, ensuring that customers get exactly what they pay for.
Goat is an online platform for luxury sneaker resellers.
Luxury sneakers are surging ahead of luxury handbags in popularity, and
the boom in counterfeits sneakers has followed. Goat resellers submit photos
of their shoes for human experts to analyze before shipping the shoes to
Goat for AI authentication.
According to Goat CTO Andy Shin, Goat has the "largest and most
comprehensive database of sneakers in the world." He also reports that as
time has gone on,
the number of fakes that Goat receives
has drastically reduced, as its zero-tolerance reputation increases.
For Entrupy, a company that specializes in luxury handbag authentication,
they rely on a higher authority, a
"convolutional neural network," which
comprises a data set of microscopic images of luxury handbags. To create
this database, they first collected bags they believed to be authentic,
dating as far back as 80 years.
Once they had enough samples, their algorithm took over,
analyzing the tiny
details that make up the DNA of the genuine articles. They posit that these
details are too difficult for counterfeiters to reproduce.
racked.com
Online shopping sites see hacking increase
despite security efforts
It's estimated eight out of 10 Americans have shopped online, entering
sensitive personal data. Credit card numbers, passwords and addresses, for
example. And that's a gold mine for cyber-criminals that hack into online
sites.
San Jose's Thales eSecurity's latest research says half -- 50 percent -- of
all medium and large online retailers it surveyed acknowledge they've been
hacked. That's two a half times higher than a year ago. Changes in payment
systems are making security more challenging.
This year alone, hackers broke into the retail sites of Adidas, Saks Fifth
Avenue, and Under Amour, according to the nonprofit group Privacy Rights
Clearinghouse.
The servers of those and all other retailers store sensitive data. That is
leading to increased spending to encrypt that data. Or to add two-factor
authentication, where a retailer will send a text message with a code to
verify it's you. A single breach can cost retailers hundreds of millions of
dollars and can impact customer confidence.
abc7news.com
Europol busts cyber crime group behind online
fraud worth £16 million
EBay deals another blow to PayPal by accepting
Apple Pay
Hy-Vee to add speedy online grocery deliveries |
|

|
|
 |
|

|
|

|
|
One Arrested in Atlanta Yesterday
Two Essex County, New Jersey, Men Charged With $600,000 Credit Card Fraud,
Identity Theft Conspiracy
Two Essex County men, with two homes, one in East Orange, N.J., and one in
Duluth, GA., were charged today for their alleged roles in a conspiracy that
used stolen personal identifying information to open credit cards and defraud a
victim bank out of approximately $600,000. One was arrested in Atlanta yesterday
morning.
They obtained the stolen personal information from other conspirators and used
it to create the fraudulent credit card accounts. Changing the address after
establishing accounts to the two homes they then along with other conspirators
used the cards at retail stores in New Jersey and Georgia, among other
places, to purchase smartphones, tablets, and other high-value items, which were
later sold for profit. Overall, the conspirators defrauded Victim Bank 1 of
approximately $600,000.
The bank fraud conspiracy charge carries a maximum potential penalty of 30 years
in prison and a $1 million fine. The aggravated identity theft charge carries a
mandatory sentence of two years in prison, which must run consecutive to any
other term imposed. The investigation is ongoing.
justice.gov
Fresno, CA: Women who struck Lululemon may be
linked to statewide crew
 A
team of women who ran out of a Lululemon store in Fresno's Fig Garden Village on
Sunday with an estimated $10,000 in merchandise may be part of a statewide crew
responsible for about $145,000 in thefts from the chain, police said Tuesday.
Videos release by police show the trio calmly strolling into the store with
large, black shopping bags, walking to shelves where the trendy attire is
displayed and quickly loading up the sportswear before making a quick exit. They
made off with an estimated 148 pairs of the pants with a retail value of $100
apiece. Lt. Joe Gomez said the crime fits the pattern of similar thefts at
stores around the San Francisco Bay Area, including Stanford, Berkeley,
Hillsdale and Gilroy.
fresnobee.com A
team of women who ran out of a Lululemon store in Fresno's Fig Garden Village on
Sunday with an estimated $10,000 in merchandise may be part of a statewide crew
responsible for about $145,000 in thefts from the chain, police said Tuesday.
Videos release by police show the trio calmly strolling into the store with
large, black shopping bags, walking to shelves where the trendy attire is
displayed and quickly loading up the sportswear before making a quick exit. They
made off with an estimated 148 pairs of the pants with a retail value of $100
apiece. Lt. Joe Gomez said the crime fits the pattern of similar thefts at
stores around the San Francisco Bay Area, including Stanford, Berkeley,
Hillsdale and Gilroy.
fresnobee.com
Costa Mesa, CA: Burglary crew hits Apple store
for $29,000 in merchandise
Costa Mesa Police are searching for five people suspected of burglarizing an
Apple store at South Coast Plaza.
Police say the suspects got away with $29,000 worth of merchandise- iPhones and
iPads that were taken from displays at the store. Police were called to the mall
about 9 p.m. Monday.
foxla.com
 Fresno,
CA: Couple arrested as suspected cigarette and lotto ticket C-Store bandits Fresno,
CA: Couple arrested as suspected cigarette and lotto ticket C-Store bandits
A couple has been arrested on suspicion of breaking into several convenience
stores in north Fresno and stealing lottery tickets and cigarettes, police said
Monday. Sierra Baize, 40, and boyfriend Keith Christenson, 30, were stopped by
police Sunday night. Baize was behind the wheel of the car that had been
identified in the burglaries, and both were arrested, Lt. Joe Gomez said.
Evidence and burglary tools were allegedly found in the car. Christensen
admitted to all six of the burglaries and Baize admitted to being the driver
during three, Gomez said.
fresnobee.com
Miami, FL: Professional Athletes and Coaches
among ID thief's victims; Indicted on 22 charges
An identity thief didn't steal just anybody's IDs - he targeted big names such
as former Miami Dolphins players Jason Taylor and Zach Thomas and former coach
Joe Philbin, Florida officials say. Michael Watters used the fraudulent IDs to
create bogus checks that he used to buy merchandise at places like Home Depot,
Target and Best Buy, then would return the goods to the same store at another
location for a cash refund. A 22-count indictment against Watters named other
victims including baseball players Johnny Damon, Jonathan Papelbon and Barry
Larkin, tennis player Jennifer Capriati and Orlando Magic player and coach Scott
Skiles.
sun-sentinel.com
Petaluma, CA: Two arrested in Target theft,
refund/gift card scheme;
hit stores in Fairfield, Vallejo and Napa
 Two
Solano County men went on a burglary spree Monday at stores in multiple cities
and ended up in the Sonoma County Jail after their arrest in Petaluma. At the
Petaluma Target store just before 7 p.m. the two attempted to steal a few
thousand dollars in merchandise, Petaluma Lt. Tim Lyons said Tuesday. They took
small appliances, clothing and other items and hid them inside large tote bags,
also on sale at the store and then tried to pay for the tote bags but not the
concealed merchandise, Lyons said. Two
Solano County men went on a burglary spree Monday at stores in multiple cities
and ended up in the Sonoma County Jail after their arrest in Petaluma. At the
Petaluma Target store just before 7 p.m. the two attempted to steal a few
thousand dollars in merchandise, Petaluma Lt. Tim Lyons said Tuesday. They took
small appliances, clothing and other items and hid them inside large tote bags,
also on sale at the store and then tried to pay for the tote bags but not the
concealed merchandise, Lyons said.
Rommel Natan, 36, and John Meurer, 40, were questioned by store security who
called police. Officers searched their car and underneath the driver's seat
found several drivers' licenses and credit cards for people in cities including
Santa Rosa, Sacramento, Fremont and Redwood City. They also found receipts dated
Monday and gift cards from stores in Fairfield, Vallejo and Napa indicating
items had been returned to those stores and exchanged for gift cards.
petaluma360.com
Harrison County, OH: Two men wanted for theft of $8,000 of
merchandise from Pawn Shop
Wetumpka, AL: Police seek woman who stole $250 worth of
underwear from Dollar General
Berkeley, CA: 13 Lululemon stores in Bay Area robbed in
past 12 days
|
|
|
|

|
|

|

|
|
Shootings & Deaths

Johannesburg, South Africa: Shoprite Security Guard shot
and killed during store robbery
A security guard was shot dead when a gang of 15 men robbed a Shoprite
supermarket in Heidelberg, south of Johannesburg on Friday evening. A video
shows the guard and one of the assailants embroiled in a scuffle at the entrance
to Ratanda Mall. As they struggled, two more robbers entered the shop. Both men
shot the security guard at close range, before more men entered the premises and
robbed it. One armed suspect was later arrested.
*Warning - graphic video
news25.com

Toledo, OH: Police Officer who shot a Dollar General
Robbery suspect 'acted within his rights'; Surveillance Video Released
Toledo Police release new information about the moments leading up to a robbery
turned deadly in our community. Police released surveillance video showing the
suspect inside the Dollar General on Heatherdowns. Detectives say the robber 56
year old Dale Slocum had a fake gun and a knife. The suspect killed 53-year-old
Tommy Thacker then took off. A Toledo police officer confronted and ended up
shooting and killing Slocum.
13abc.com
Farmersville, CA: Liquor store owner allegedly
shoots two, himself inside store
A liquor store owner in Farmersville was arrested Tuesday, after allegedly
shooting two people and himself inside the store, police say. When Farmersville
officers arrived to Aztec Liquor at 686 E. Visalia Road just after 1 p.m., they
found owner Harbhajan Singh Mundi, 61, had allegedly shot himself in the foot
accidentally. They also found two other men. One was shot in the body and was in
serious condition, and the other was also shot in his foot, police say. They
were all treated for their injuries. Police say Mundi had been arguing with the
property owner in an ongoing dispute when the shots were fired. The property
owner and several other people went to the store to meet with Mundi, police say.
fresnobee.com
Robberies, Incidents & Thefts

Nacogdoches, TX: Walmart Market Shoplifter assaulted
Police Officer, attempted to take weapon
Monday evening, Latoya Mae Pickard, 35, was arrested on a second-degree felony
assault of a public servant charge, a state-jail felony attempting to take a
weapon from officer charge, and Class B misdemeanor theft. When an officer made
contact with Pickard, she assaulted the officer and caused minor injuries to him
or her, the report stated. During the struggle, Pickard also allegedly tried to
take one of the NPD officer's weapons.
ktre.com
Prince William County, VA: 7-Eleven Armed Robbery suspects
wreck get-a-way car on I-95
Woodland, WA: Police and Cowlitz County Sheriff's deputies
catch Shoplifting suspect with Drone and K9 unit
 Fire & Arson Fire & Arson
Minneapolis, MN: Marshalls still closed after
suspected arson causes over $500,000 in damage
The Marshalls store in downtown Minneapolis' City Center building has been
closed for more than a week following a reported arson that damaged hundreds of
thousands of dollars worth of inventory. On July 15, a customer allegedly set
fire to a display rack and caused over $500,000 in damage to store clothing,
according to a Minneapolis Fire Department report. By time the fire department
personnel arrived to the City Center store at the 600 Nicollet Mall block, the
fire was out. There were no injuries reported. There have been no arrests,
though police have both video evidence and suspect information, said Minneapolis
Police Department Sgt. Darcy Horn.
bizjournals.ocm |
| |

|
|
•
Adult Store - Houston, TX - Robbery
•
Boost Mobile - Miami, FL - Burglary
•
C-Store - Atoka, OK - Armed Robbery/Shooting - Clerk
wounded
•
C-Store - Fresno, CA - Burglary
•
Cash Express - Owensboro, KY - Armed Robbery
•
Family Dollar - Clifton, NJ - Armed Robbery
•
Liquor Store - Lawrence, KS - Armed Robbery
•
Lululemon - Fresno, CA - Robbery
•
Pharmacy - Adamsville, AL - Robbery
•
Restaurant - Neptune Beach, FL - Armed Robbery
•
T-Mobile - Opelika, AL - Armed Robbery
•
Verizon - Memphis, TN - Armed Robbery
•
Wawa - Lexington Park, MD - Armed Robbery
•
Walgreens - Jefferson City, MO - Armed Robbery
•
Walgreens - Dayton, OH - Robbery
•
Walmart - Nacogdoches, TX - Robbery/ Assault on Police
Officer
•
Walmart - Monroe, NJ - Robbery
•
7-Eleven - Henrico County, VA - Armed Robbery
•
7- Eleven - Cape Coral, Fl - Armed Robbery
•
7-Eleven - Lowell, MA - Armed Robbery
|
|
|
Daily Totals:
•
18 robberies
•
2 burglaries
•
1 shooting
•
0 killings
|
|
 |
|

|
|
|
|
None to report. |
|
Submit Your New Hires/Promotions or New Position
|
|

|
|
 |
|

|
|

|
|
Featured Job Spotlights
 |
Vice President, Asset Protection
Columbus,
OH
Oversees and directs all Asset Protection
related functions for a Corporate Office, multi-state distribution centers and
large retail store network. Responsible for enterprise direction and strategy as
it pertains to Asset Protection with a goal of minimizing shrink, reducing loss
and maximizing security and associate safety...
|
NEW TODAY
 |
Vice President Loss Prevention
Memphis, TN
The Vice President Loss Prevention is responsible for providing
direction, development and leadership to Loss Prevention, Safety, Security and
Audit teams for corporate, distribution centers and the field... |
 |
Director of North America Digital Risk & Control
Beaverton, OR
As the Director of North America Digital Risk & Control, you will
provide leadership for payment risk mitigation in our digital business including
fraud risk management. You will be responsible for ensuring our resources and
capabilities are properly aligned to the execution of key priorities, as you
develop and implement ecommerce risk management strategies to appropriate
tolerance levels based on advanced data analytics and trends...
|
 |
Director of Data Privacy and Security, Legal
Los Angeles, California
As Netflix continues to grow and expand, we are looking for a talented team
member to join the Data Privacy and Security Legal team to provide support on
privacy and data security compliance matters. The position will report to the
Global Director of Data Privacy and Security, and will work in an ongoing and
collaborative way with relevant Legal, Security and Public Policy groups in
carrying out her or his responsibilities...
|
NEW TODAY
 |
Director, Risk Management and Safety
Los Angeles, CA
To protect the company's global assets and property from risk of
loss via the purchase of insurance and by implementing a global risk management
program in the most cost efficient and effective manner...
|
 |
Financial Analyst (Internal Fraud)
Anaheim, CA
This role is responsible for investigating internal
fraud and Cast Privilege abuse at the Disneyland Resort, across all lines of
business including but not limited to: merchandise, food & beverage, rooms,
ticketing, and employee privileges. Specific investigative tasks will vary but
may include: reviewing exception reporting to identify potential fraud trends,
conducting in-depth point-of-sale research, reviewing camera surveillance,
performing integrity shops and observations, interviewing employees,
representing the Company at grievances and unemployment hearings, and partnering
with law enforcement as needed...
|
NEW TODAY
 |
Regional Loss Prevention Manager
Pacific Northwest
Job responsibilities include, but are not limited to the following:
● Conducts internal investigations related to theft, business abuse, and safety
violations by conducting interviews, determining course of action, and writing
reports.
● Formal interview training, i.e. Wicklander-Zulawski or Reid Techniques...
|
|
 |
Regional Safety & Loss Prevention Specialist
Baltimore, MD
The Safety and Loss Prevention Specialist is a subject
matter expert responsible for partnering with both our corporate TUSA stores and
franchise store operations to improve the safety and training processes... |
 |
Area Loss Prevention Specialist
Boston/Springfield
We are currently
looking for an Area Loss Prevention Specialist to join our team in the Boston /
Springfield area. This position is responsible for conducting employee
investigations, responding to and providing guidance during critical incidents,
and assessing new/current retail store locations...
|
 |
Area Loss Prevention Specialist
Jacksonville, FL
We are currently looking for an
Area Loss Prevention Specialist to join our team in Jacksonville, FL. This
position is responsible for conducting employee investigations, responding to
and providing guidance during critical incidents, and assessing new retail store
locations...
|
 |
Area Loss Prevention Specialist
San Francisco Bay Area
We are currently looking for an
Area Loss Prevention Specialist to join our team in San Francisco Bay Area. This
position is responsible for conducting employee investigations, responding to
and providing guidance during critical incidents, and assessing new/current
retail store locations...
|
Featured Jobs
To apply to any of today's Featured Jobs, Click Here

|
|
 |
|

|
|

|
|
Today's
Daily Job Postings from all around the net - Appearing today only
To apply to today's Internet Jobs, Click Here
|
|
Sponsor Today's Internet Jobs |
|

|
|

|
|
Become a Better Leader:
Secrets from
Santa Claus,
5 Leadership Principles, Master Multiple Leadership Styles
|
|
|
|

|
|
 |
|

|
|

|
|
When giving references it is best not to comment on someone if
you haven't worked directly with them. Passing on third party information can be
extremely detrimental to the employer and the job seeker. If an employer is
going to the extent of conducting references and is considering making an
investment in an executive than the process warrants direct information that can
help both the employer and the job seeker in reaching their decisions. And as
most know third party information is extremely unreliable and can cause both
parties to make mistakes.
Just a Thought,
Gus
 |
|
We want to post your tips or advice... Click here |
|

|
|

|
|
Not getting the Daily? Is it ending up in your spam folder?
Please make sure to add d-ddaily@downing-downing.com to your contact list,
address book, trusted sender list, and/or company whitelist to ensure you
receive our newsletter.
Want to know how?
Read Here |
|
|
|

|
|
 |








_2.jpg)














.jpg)







.jpg)






































 "This is a huge business opportunity," says David Hyde, when asked how the
upcoming legalization of recreational cannabis under The Cannabis Act will
impact the security business.
"This is a huge business opportunity," says David Hyde, when asked how the
upcoming legalization of recreational cannabis under The Cannabis Act will
impact the security business.