|
Taking a New Approach: Trust No One
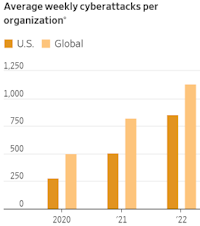
Weakest link in security, as it’s been since the Trojan War, is humans.
The philosophy, known as zero-trust architecture,
assumes that no matter how robust a company’s external defenses are,
hackers can get in. So companies need to make sure that even users inside a
network can’t do serious damage.
&uuid=(email)) What
many of these recent hacks have in common is that they
succeeded by tricking a person in or close to the target company into
giving up network-access credentials or other critical information, a technique
known as social engineering. What
many of these recent hacks have in common is that they
succeeded by tricking a person in or close to the target company into
giving up network-access credentials or other critical information, a technique
known as social engineering.
 The
hacks at the two companies, which declined to discuss their approach to
security, are increasing the push for zero-trust within their peer group.
Zero-trust is a broad concept, but at base
it means that no part of a company’s IT systems should assume that any other
part—human or software—is who or what it claims to be. All systems are
assumed to be compromised by hackers already. The
hacks at the two companies, which declined to discuss their approach to
security, are increasing the push for zero-trust within their peer group.
Zero-trust is a broad concept, but at base
it means that no part of a company’s IT systems should assume that any other
part—human or software—is who or what it claims to be. All systems are
assumed to be compromised by hackers already.
As big and well-resourced companies have gotten better at protecting against
purely technical exploits of their systems, these social-engineering attacks
have become more popular, say cybersecurity experts and the
Federal Bureau of Investigation. It is, after all, easier to upgrade a
computer than the human mind.
Every component of a system should be skeptical that you are who you say you
are and are doing what you should be doing.
Many of the design principles that guide engineers building
zero-trust systems are easy to understand.
From forcing users to log back in - "rotating", to behavioral analysis of
out-of-character credit card purchases.
Zero-trust systems can create friction for users and employees, because
security is always a balance between giving people the access they need and
demanding that they prove their identity. This is also by design, a concept
known as the “principle of least privilege,” or giving people access only
to the things they need, when they need them, and no more.
While many businesses are only now adopting true zero-trust systems, the
security industry has been talking about the trust problem for well over a
decade.
Even proponents acknowledge that zero-trust is no silver bullet, in no small
part because it takes so much time and effort to make it a reality. But in a
world where
regulators,
shareholders and
customers are all ready to hold companies and their leaders accountable
for hacks and data breaches, and attackers are more resourceful and aggressive
than ever, companies might not have much choice.
They have to commit to making themselves less vulnerable.
“The new world is, you’ve got to assume there are always going to be bad people
on your network,” says Mr. Boitano of Nvidia. “And the question is how do you
protect your resources and the intellectual property of the company.”
wsj.com
|