|
Five US retail chains are
now banning the open carry
of guns in their stores
Every week seems to bring a fresh installment of "patch or perish."
For those not in the know, that vulnerability cat-and-mouse game goes like this:
IT teams race to test and apply newly released, critical updates to software and
systems - under cover of mitigating or compensating controls - before hackers
create and field working exploits for the flaws the patches fix.
Such efforts continue nonstop.
Risk Based Security's VulnDB team, for example, counted 11,092 newly
disclosed vulnerabilities during the first half of 2019. Public exploits existed
for 34 percent of those flaws, 53 percent of all of the vulnerabilities could be
exploited remotely and nearly 5 percent of all of the bugs also affected
security software.
Some weeks are worse than others. The U.S. Cybersecurity and Infrastructure
Security Agency, in its
vulnerability summary for the week of Aug. 19, released Aug. 26, described
nearly 600 new vulnerabilities, or about 20 percent more than in the average
week. Flaws included 49 serious vulnerabilities in software developed by Adobe,
Google Android, IBM as well as for WordPress, plus 170 medium-severity flaws,
eight low-severity flaws and 360 vulnerabilities for which no severity had yet
been assigned.
Risk-Management Challenge
Security experts warn that patch management, or the larger question of
vulnerability management, must be part of a much bigger-picture approach to
managing risk.
"I don't see much written on vulnerability management in more holistic terms
versus patch/bug fixing," says
Phil Venables, a board director and senior adviser for risk and
cybersecurity at Goldman Sachs Bank, via Twitter. "I've always found it
immensely useful to think of vulnerability management as four layers, building
on each other and in turn becoming more powerful as a risk mitigation approach."
Here are his four layers of vulnerability management:
-
Basics: Ensure the vulnerability management team has complete coverage
of the organization and that it ranks the criticality of each flaw and also
maps all system dependencies.
-
Components: Discover and remediate component flaws. This is the most
well-known component of vulnerability management.
-
Configuration: Discover and remediate configuration flaws.
-
Architecture: The highest layer involves "architectural goal enumeration
and enforcement," he says. This includes identifying necessary constraints,
such as "developing rules for what potentially toxic arrangements of
components should never exist," and then ensuring that the vulnerability
management team is tasked with monitoring for these continuously. Likewise,
such a program should identify obligations, including "developing default
architectural/design patterns for the deployment of common services and then
monitoring for adherence to those," as well as enforcing their use
throughout the software development life cycle.
Failing to patch the right system at the right
time - or to otherwise mitigate flaws - can have massive repercussions. Equifax,
for example, instructed all IT personnel to ensure they'd installed a critical
patch for all Apache Struts implementations, but then failed to confirm that all
Struts systems had actually been patched. In the interim, attackers quickly
infiltrated its systems, installing 30 web shells for remote access and
exfiltrating massive quantities of data (see:
Equifax Breach 'Entirely Preventable,' House Report Finds).

As Venables has also noted,
many security incidents "are not due to a lack of conception of controls but
due to failures of expected controls," which may include patch management. As a
result, he says controls must be continuous monitored and validated, with any
failures being treated as security incidents themselves.
Start Here: 'Do We Have It?'
Organizations can't patch what they don't know about. Conversely, they can't
make a well-calculated decision about what to fix first - or temporarily
postpone fixing - as well as what they can safely ignore.
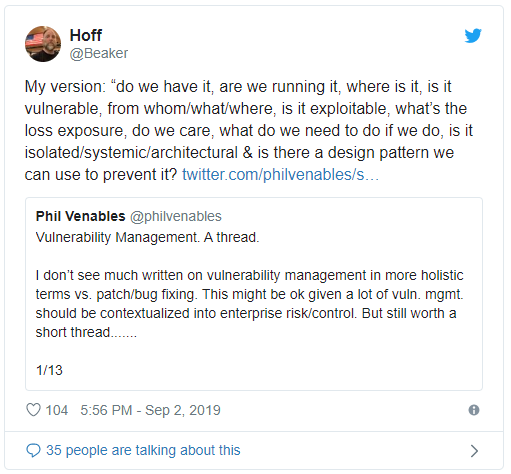
Such thinking is the cornerstone of the
exposure management and assurance process practiced by Chris Hoff (@Beaker),
CISO for Chicago-based financial services firm Citadel.
His vulnerability management team learns to dream the following questions in
their sleep, he says: Do we have it? Are we running it? Where is it? Is it
vulnerable? From whom/what/where is it exploitable? What's the loss exposure? Do
we care? What do we need to do if we do? Is it isolated/systemic/architectural
and is there a design pattern we can use to prevent it?
Patching Lags
Despite such guidance, the failure to rapidly patch systems is widespread, based
on the number of vulnerable systems that remain.
In recent weeks, for example, warnings have
intensified over the many
unpatched SSL VPNs manufactured by Pulse Secure and Fortinet. Security
experts say attackers have been running large-scale scans to identify machines
that have yet to be updated with patches released in April and May. Attackers
can exploit the flaws to steal data, including passwords, and obtain
unauthenticated, remote access to enterprise networks (see:
Chinese APT Group Began Targeting SSL VPN Flaws in July).
Waiting for BlueKeep Attacks
Or take the calm before the storm regarding the BlueKeep vulnerability in older
versions of the Windows operating system (see:
Weaponized BlueKeep Exploit Released).
On May 14, Microsoft pushed patches for the vulnerability (CVE-2019-0708) that
attackers can exploit to compromise Remote Desktop Services in Windows and gain
full, remote access to a system, including full administrator privileges and the
ability to execute arbitrary code. Last month, Microsoft warned that
BlueKeep exploit code is in the wild. But many organizations have been
slow to patch.
"Patching, or rather good cyber hygiene, is an integral component of every
company's defense against cyberattacks,"
Raj Samani, chief scientist at McAfee, recently told Information Security
Media Group.
The number of systems that have yet to receive the RDP patch that safeguards
against BlueKeep attacks "shows that the fundamentals of good cyber hygiene
remain overlooked for so many companies," he said.
Many CIOs and CISOs, however, have for years been trying to tackle the patch,
vulnerability and risk management challenges, only to see them continue to grow
more complex.
"In a sentence, dependency management has gotten a lot harder," Venables tells
ISMG.
Article originally published on
govinfosecurity.com
|